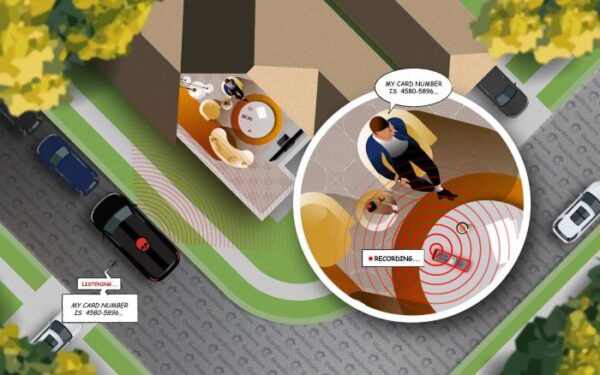
Voice control can always become a privacy threat as soon as it lands on to the hands of perpetrators. Recently, researchers found a vulnerability in Comcast XR11 voice remote controller that could allow eavesdropping on the users.
Comcast Voice Controller Vulnerability
Researchers from Guardicore found a serious security vulnerability affecting Comcast voice controllers. Whilst exploiting the bug, they came up with the attack “WarezTheRemote” that allowed eavesdropping.
Sharing the details in a blog post, the researchers revealed that the said attack strategy could allow an attacker to transform the device into a spy tool.
Briefly, they found the vulnerability in Comcast XR11 voice remote controller. It comes with a microphone to let the user give voice commands and communicates with the set-top box via radiofrequency (RF) instead of the more common infrared (IR).
While RF is convenient as it works from greater distances, the same also increases the attack surface.
Besides, the remote controllers also exhibited OTA firmware updates that don’t require signatures for the remote to install. Hence, it became possible for an attacker to upload malicious firmware updates turning the device into a spy tool. Then, due to the larger radius of the RF, the attacker could listen to the users’ activities from faraway.
Upon reverse engineering the firmware, the researchers found that the XR11 firmware communicates with the set-top box via the secure RF4CE (Radio Frequency for Consumer Electronics) protocol. This protocol supports packet-by-packet encryption when implemented within the firmware.
However, the firmware didn’t check whether the responses received to encrypted requests are also encrypted. Rather it also accepted responses in plain text.
Hence, an attacker could easily exploit this issue to upload malicious firmware to the remote.
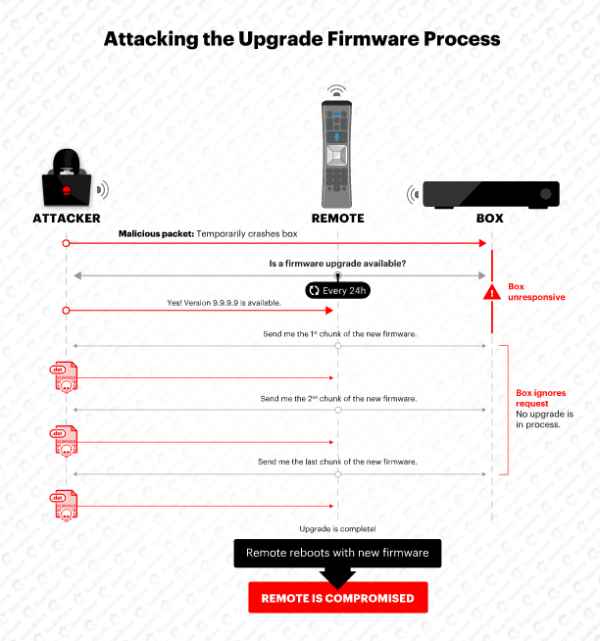
Source: Guardicore
Exploiting the flaw, the researchers didn’t only meddle with the firmware, but could also crash the cable box via DoS.
The researchers have shared the details of the attack in a research paper, whereas the following video demonstrates the PoC.
Fixed Rolled Out
Guardicore discovered the vulnerability and came up with WarezTheRemote back in April 2020. As they observed, the attack had no other mitigation except removing the batteries of the vulnerable devices.
They eventually reached out to Comcast to report the matter.
And, finally, in September 2020, Comcast confirmed to have patched all vulnerable devices as they rolled out patch 1.1.4.0. As confirmed in their statement,
We fixed this issue for all affected Xfinity X1 Voice Remotes, which means the issue described here has been addressed and the attack exploiting it is not possible.
(Nonetheless, the threat to IoT security still persists.)