Digitally signed PDF documents are considered as valid as docs with manual signatures. However, a recently discovered attack threatens the legitimacy of this technique. Researchers have found Shadow attacks that allow modifying the content within digitally signed PDFs.
Shadow Attacks Threaten Signed PDFs
Researchers from the Ruhr University Bochum, Germany, have devised a new strategy that allows meddling with PDFs. Dubbed Shadow attacks, the researchers have come up with multiple attack techniques that allow changing the content of digitally signed PDFs.
Specifically, these attacks exploit the legitimate features that keep the target documents compliant with the standards. Thus, shadow attacks bypass all existing strategies that detect any malicious editing attempts on PDFs.
In brief, these attacks work on the idea of how people use PDF documents and digital signatures today.
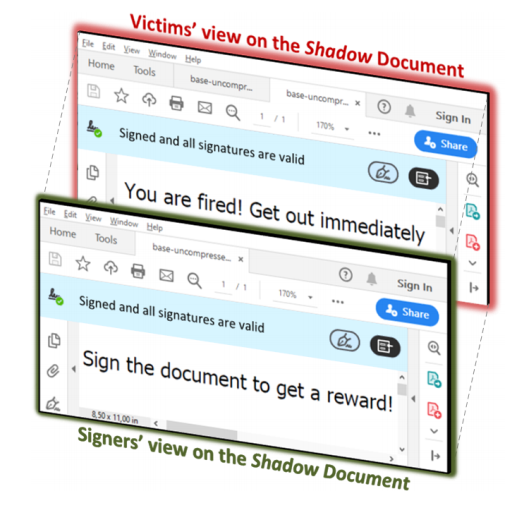
In a real-world scenario, somebody prepares a document with some content that the two parties subsequently review before signing. Likewise, Shadow attacks let an adversary create a malicious document that hides the attackers’ intended content behind the legit one.
When the first party reviews the document, the content appears fine. Hence, the signer signs it. After that, the attacker would meddle with the content, thus the second party would see different content.
As the researchers explained,
The attackers prepare a shadow document. In the analog world, this is the step in which the attackers could explicitly leave empty spaces. The Signers of the PDF receive the document, review it, and sign it. The attackers use the signed document, modify it, and send it to the victims. In the analog world, the attackers can print their content on the prepared empty spaces. After opening the signed PDF, the victims’ PDF viewer successfully verifies the digital signature. However, the victims see different content than the Signers.
The adversary can proceed with these attacks from three different approaches; hide, replace, and hide-and-replace.
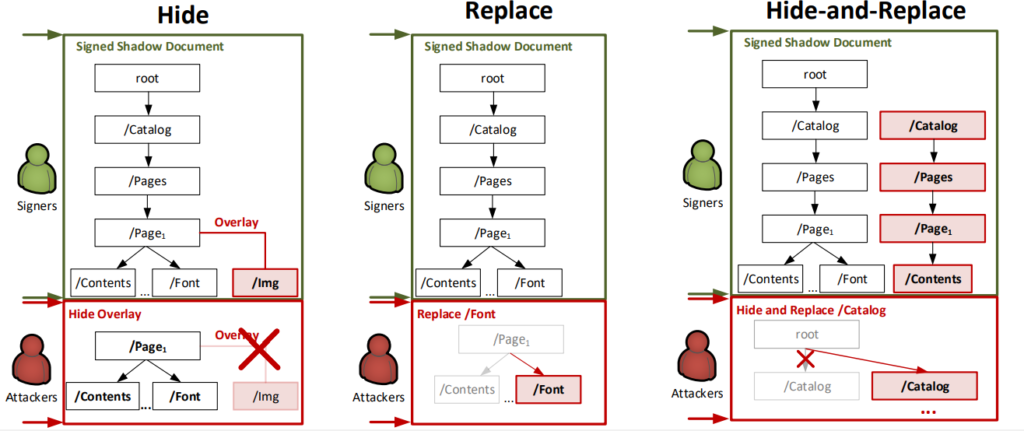
Source: Rohlmann et al.
These attacks require no loading of content from external sources or running scripts. Nor do they invalidate digital signatures or trigger warnings. Hence, detecting these attacks remains difficult.
What Next?
Previously, similar attacks targeting signed PDFs surfaced online in 2019 by Mladenov et al. However, following that research, almost all PDF viewers implemented strategies mitigating such attacks.
However, all of the existing security measures appeared useless in case of Shadow attacks.
The researchers tested 29 different PDF viewers during their study. From these, they found 16 of them fully vulnerable to Shadow attacks, including Foxit Reader and Adobe Acrobat. Whereas, the other
They have also introduced PDF-Attacker, a tool that automatically exploits these attacks. Yet, they have rolled out PDF-Detector as well that detects Shadow attacks.
Before public disclosure, the researchers coordinated with the respective vendors via CERT-Bund. In turn, 15 of these implemented quick fixes and now remain safe from Shadow attacks. These include the popular tools Adobe, Foxit, LibreOffice, Power PDF, and Soda PDF.
However, the researchers doubt that 11 other tools; Master PDF in Windows and Linux, Nitro Pro, PDFXChange Editor, Perfect PDF Reader, Expert PDF 14, Nitro Reader, PDF Editor 6 Pro, Perfect PDF 8 Reader, and Perfect PDF 10 Premium, may remain vulnerable.
Technical details of shadow attacks are available in the researchers’ research paper that they have presented recently at the Network and Distributed System Security Symposium (NDSS) 2021.