Telegram users need to remain careful as cybercriminals are running malicious campaigns via Telegram bots. Researchers found these Telegram bots steal one-time passwords (OTP) on target devices to compromise online accounts.
Malicious Telegram Bots Steal OTP
Researchers from Intel471 have found cybercriminals using Telegram bots to steal users’ OTP in new malicious campaigns.
As elaborated in their blog post, the hackers attempt to bluff users by impersonating various legit services (such as banks).
The malicious services have been active since June where the hackers abuse Telegram bots to reach victims while mimicking customer support. Usually, different criminal users boast the money they make via these bots in various Telegram channels.
Among these, SMSRanger works against various slash commands to provide the instructions.
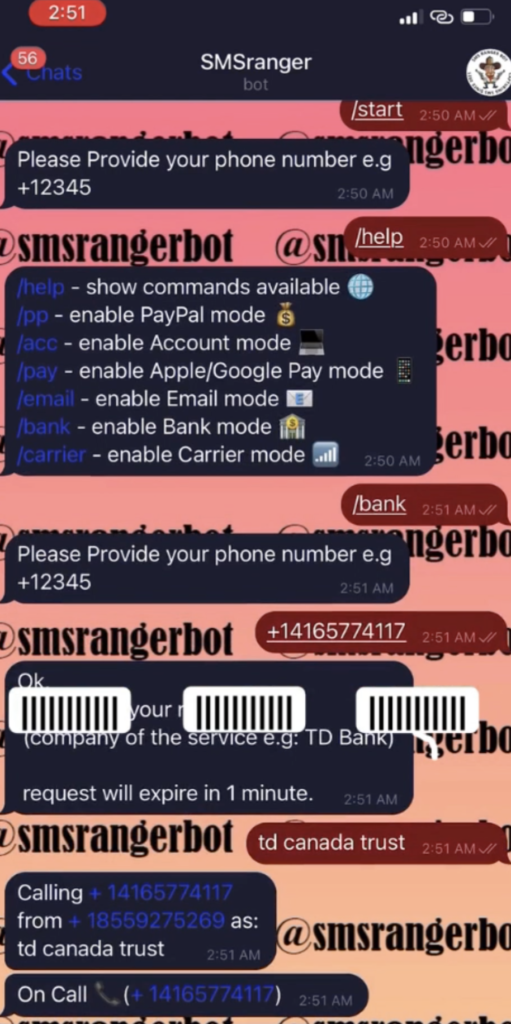
SMSRanger bot command module (Source: Intel471)
It then begins its activity after getting the target users’ phone numbers.
Once a target’s phone number has been entered, the bot does the rest of the work, ultimately granting access to whatever account has been targeted. Users claim that SMSRanger has an efficacy rate of about 80% if the victim answered the call and the full information (fullz) the user provided was accurate and updated.
Likewise, BloodOTPbot is also a paid tool that targets victim’s OTPs via social engineering tactics. An adversary needs to subscribe to it for $300/month to wage phishing campaigns.
Whereas another bot, SMS Buster, seeks more information to conduct legit-looking fake calls. Specifically, it requires the attacker to enter the caller number to display, the victim’s phone number, the bank to impersonate, and the first name for the caller agent. It then lets the adversary start the attack.
From there, an attacker could follow a script to [trick] a victim into providing sensitive details such as an ATM personal identification number (PIN), card verification value (CVV), and OTP, which could then be sent to an individual’s Telegram account.
The researchers recommend strengthening OTP verification strategies by using robust methods like time-based OTPs (TOTPs) via authenticator apps, push-notification-based codes, or FIDO security keys.

