A team of academic researchers has devised a new user tracking strategy. Dubbed “DrawnApart”, this technique employs GPU fingerprinting to identify their devices.
DrawnApart GPU Fingerprinting
Briefly, DrawnApart is a hardware-based fingerprinting strategy identifying users via the GPU stack of their devices.
According to the researchers, the existing fingerprinting techniques cannot serve fingerprinting purposes for a long time. That’s because those techniques primarily rely on browser fingerprints, which may change over time. Hence, such fingerprints may get mixed with other fingerprints sharing hardware or software similarities.
Nonetheless, DrawnApart addresses this gap by fingerprinting device GPU. Specifically, the technique involves logging the speed variations between the GPU Execution Units (EU). Such fingerprinting can even distinguish between two fingerprints apparently sharing similar hardware. Also, it is easy to execute via a simple unprivileged JavaScript.
Explaining the significance of this study, the researchers state,
On the conceptual front, it is the first work that explores the manufacturing differences between identical GPUs and the first to exploit these differences in a privacy context. On the practical front, it demonstrates a robust technique for distinguishing between machines with identical hardware and software configurations, a technique that delivers practical accuracy gains in a realistic setting.
Regarding how DrawnApart works, briefly, it involves generating multiple rendering tasks aimed at specific EUs and tracking the time. Then, using a deep learning algorithm, the subsequent fingerprint trace generated by the time lags, now transformed into an embedding vector, can uniquely identify the device generating it.
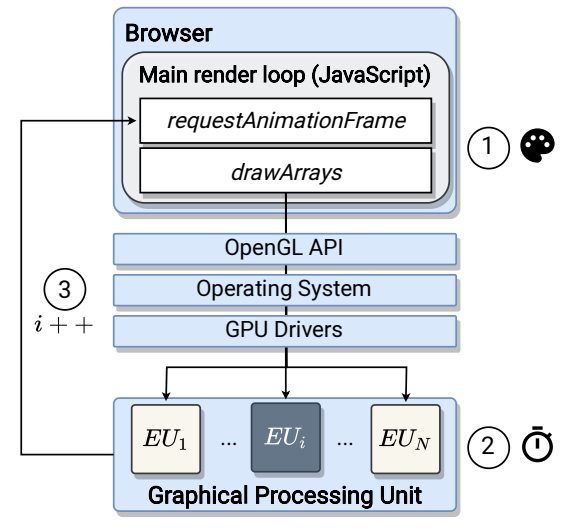
GPU fingerprinting overview (Source: Laor and Mehanna et al.)
In their study, the researchers could successfully collect data from 2500+ devices over several months. They noticed a 67% increase in the median tracking duration compared to the existing tracking algorithms.
The researchers have elaborated on their study in a detailed research paper.
Suggested Countermeasures
While DrawnApart is an effective GPU fingerprinting technique, researchers have shared a few measures to prevent such methodologies.
The first of these is blocking scripts via adblockers or browser settings since DrawnApart typically relies on JavaScript. Then, changing attribute values to unify fingerprints (such as the Tor browser does already), blocking API, preventing parallel execution by disabling hardware-accelerated rendering, and including a randomization step to the GPU dispatcher can effectively help prevent such tracking.

