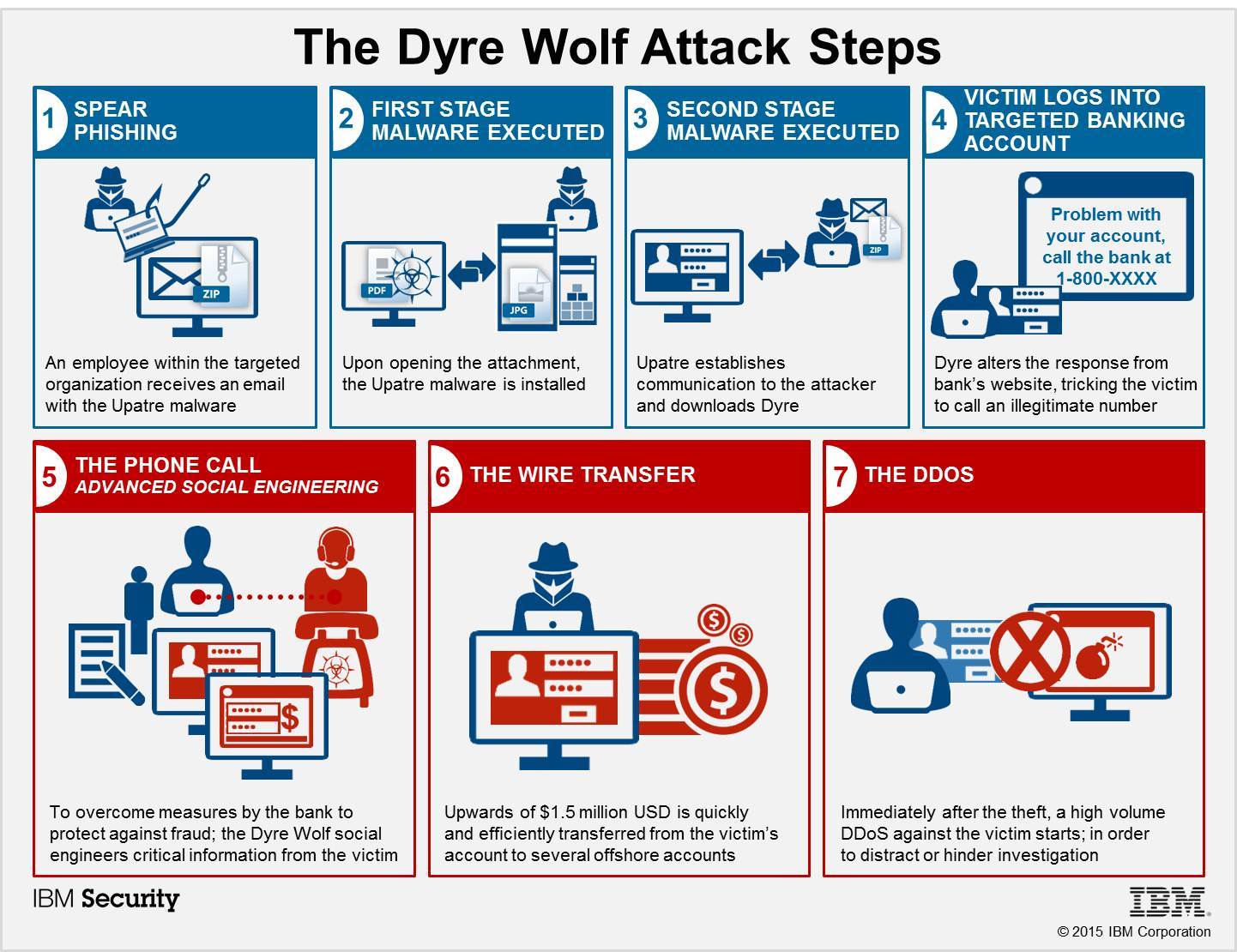
An active campaign using a variant of the Dyre malware has successfully stolen over $1 million from a variety of targeted enterprise organizations using spear phishing emails, malware and social engineering tricks.
The campaign, named “The Dyre Wolf” by IBM Security researchers, shows a brazen twist from the once-simple Dyre malware by adding sophisticated social engineering tactics likely to circumvent two-factor authentication,according to a blog post.
The organizations have lost between $500,000 and $1.5 million each to attackers—and the malware infection rate continues to increase.
How it works :
This campaign highlights the fact that organizations are only as strong as their weakest link, and in this case, it’s their employees. IBM’s Cyber Security Intelligence Index indicated 95 percent of all attacks involved some type of human error.
How to protect against the Dyre Wolf Attack :
- Organizations should train its employees on security best practices.
- Conduct periodic mock phishing exercises where employees receive emails or attachments that simulate a malicious behavior. Then using that findings, discuss the growing security threats with them.
- Provide security trainings to its employees in order to help understand threats and measures they can take to protect their organization.
- Regular reminders on phishing and spam campaigns should be provided to employees in order to prevent them to open any suspicious attachments or links.
- As the banks never ask for banking credentials, employees should be trained to never provide this information to anyone.