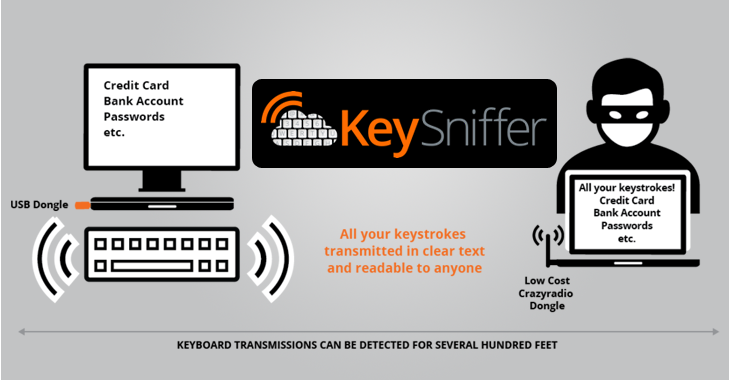
Radio-based wireless keyboards that use a special USB dongle to communicate with your PC can expose all your passwords, credit card numbers and everything you type. Hackers can now easily intercept everything you type and also can even inject malicious commands in the stream of keystroke data.
The security vendor – Bastille has discovered this vulnerability which they nicknamed KeySniffer, affects wireless keyboards from vendors such as Anker, EagleTec, General Electric, Hewlett-Packard, Insignia, Kensington, Radio Shack, and Toshiba.
Main Cause For This Security Flaw :
All the affected wireless keyboards use cheap transceiver chips (non-Bluetooth chips) – a less secure, radio-based communication protocol and that is why it is vulnerable to KeySniffer. The issue with these chips is that they don’t receive Bluetooth’s frequent security updates.
Moreover the affected keyboards use unencrypted radio transmission so anyone within 100 meters range of your computer and around $15-$30 long-range radio dongle can intercept the communications between affected wireless keyboards and your computer. By this hackers can easily access your entire computer and get all your personal details whatever u type in, for example your credit card details or even your password.
The transceivers used in wireless keyboards vulnerable to KeySniffer are inherently insecure due to a lack of encryption, and do not support firmware updates, Bastille explains.