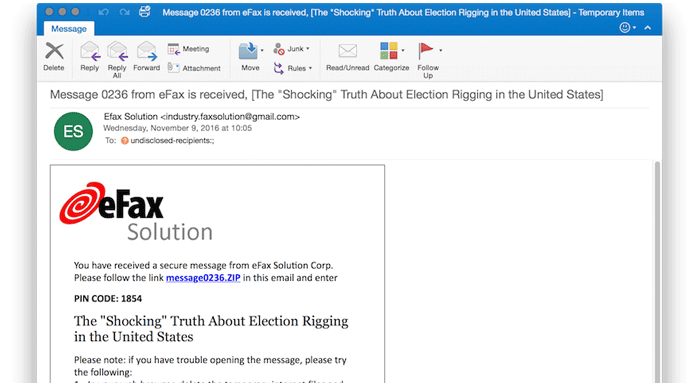
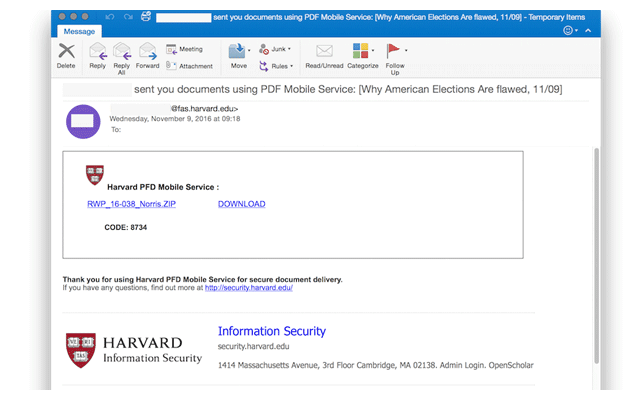
The group of nation-state hackers known by various names such as Cozy Bear, APT29, and CozyDuke sent a series of phishing emails to dozens of targets associated with non-governmental organizations (NGOs). All this phishing attack from attackers was just a few hours after Donald Trump won the 2016 US Presidential Election.
The phishing emails were sent from purpose-built Gmail accounts and other compromised email accounts at Harvard University’s Faculty of Arts and Sciences (FAS), trying to trick users into opening the attachments containing malware and clicking on malicious links.
Hackers took advantage of this curiosity to target users using phishing emails, especially the people who worked for the Government of America.