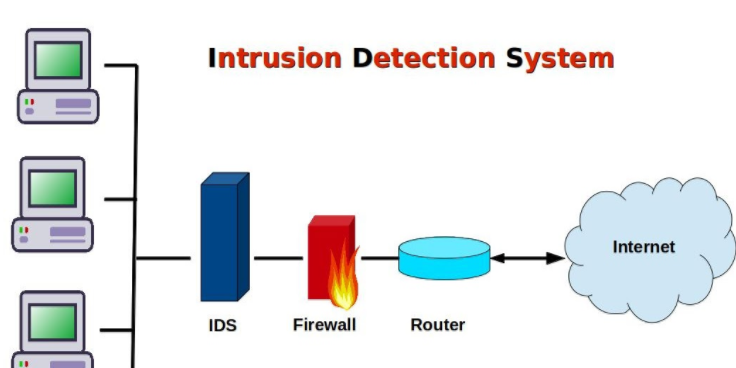
There are many types of IDSs (intrusion detection systems) to choose from. The first thing you require to do is study the computer assets you want to secure and recognize the most important computer assets that should get a higher level of security support. These machines are regularly the simplest ones to use when making an ROI case to management. New intrusion detection system administrators should begin small, learn, fine-tune, and then grow.
Don’t try to boil the ocean. A HIDS (Host-based intrusion detection systems) should be used when you want to secure a particular valuable host asset. A NIDS (network intrusion detection systems) should be used for general network awareness and as an early warning detector across various hosts.
You must choose an IDS that supports your network topology, operating system platforms, resources, and experience. If you have an important amount of wireless traffic uncovered in public areas, consider investing in a wireless IPS. If you have high-speed links that you need to monitor, make sure your IDS has been evaluated and tested at the same traffic levels.
Should your IDS be based on abnormality or signature detection? If it’s possible, use a product that based on both. The best IDSs use all methods, merging the strengths of each kind to give a greater security strategy.