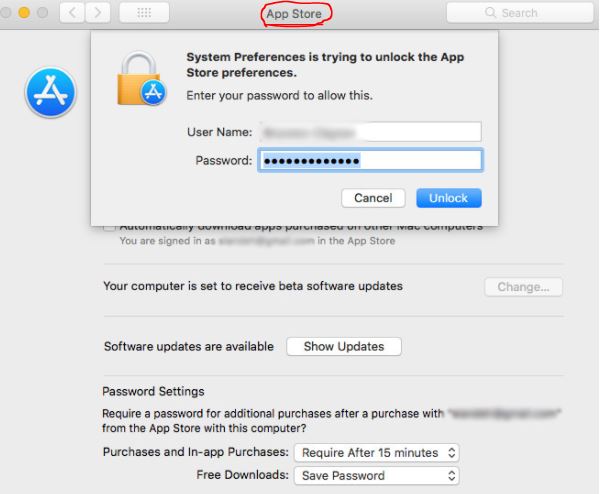
A new vulnerability has been found in macOS version 10.13.2 that enables anyone with access to your Mac to unlock App Store system preferences using any username and password as long as you are logged in as a local admin.
This means that if your account is an admin and you leave the machine unattended, anyone with malicious intent can change the App Store settings on the Mac without your knowledge.
The bug has been reported on Open Radar from earlier this week, the vulnerability enables any user to change the App Store system preferences with any password, in five steps or less:
“Steps to Reproduce:
1) Log in as a local admin
2) Open App Store Prefpane from the System Preferences
3) Lock the padlock if it is already unlocked
4) Click the lock to unlock it
5) Enter any bogus password”
According to Mac Rumors, Apple has fixed this issue in the latest beta of macOS 10.13.3, which currently remains in testing and will likely be published at some point this month. This issue doesn’t exist in macOS Sierra version 10.12.6 or earlier.
Users are not recommended to use a local admin account and make sure to lock the mac when it is not being used.