Despite continuous threats of hacking and cyber attacks, companies keep failing to provide adequate security to their customers. Every now and then, we hear reports about data leaked or left exposed on unprotected servers. In fact, the Amazon S3 bucket leak incidents keep growing exponentially. This time, this vulnerability has oddly affected spyware firm SpyFone. The firm exposed terabytes of customers’ data on the unprotected server.
SpyFone Exposed Personal Data Of Thousands Of Customers Online
As disclosed by Motherboard, a cellphone spyware company SpyFone allegedly exposed a massive database of its customers online. SpyFone is a spyware company that offers parental monitoring apps for parents and employers. Ironically, the company left terabytes of data belonging to thousands of its customers on an unsecured server.
The leaked data includes extensive personal details of the customers. The matter surfaced online after an anonymous security researcher discovered this data last week on an Amazon S3 bucket. As stated by Motherboard,
“The data exposed included selfies, text messages, audio recordings, contacts, location, hashed passwords and logins, Facebook messages, among others.”
In addition, as disclosed by the researcher who preferred to remain anonymous, the leaked data also includes terabytes of unencrypted photos.
“There is at least 2,208 current customers and hundreds or thousands of photos and audio in each folder. There is currently 3,666 tracked phones.”
The researcher also communicated with Troy Hunt of HaveIBeenPwned.com. Based on the provided information, he then indexed around 44,109 breached SpyFone accounts in the database.
The Irony Continues…
Besides exposing the data on an unprotected server, the researcher also noticed some more “irresponsible” practices at SpyFone. According to him, the company’s website had an open backend as well. Thus, he could easily create an admin account and view the customers’ data!.
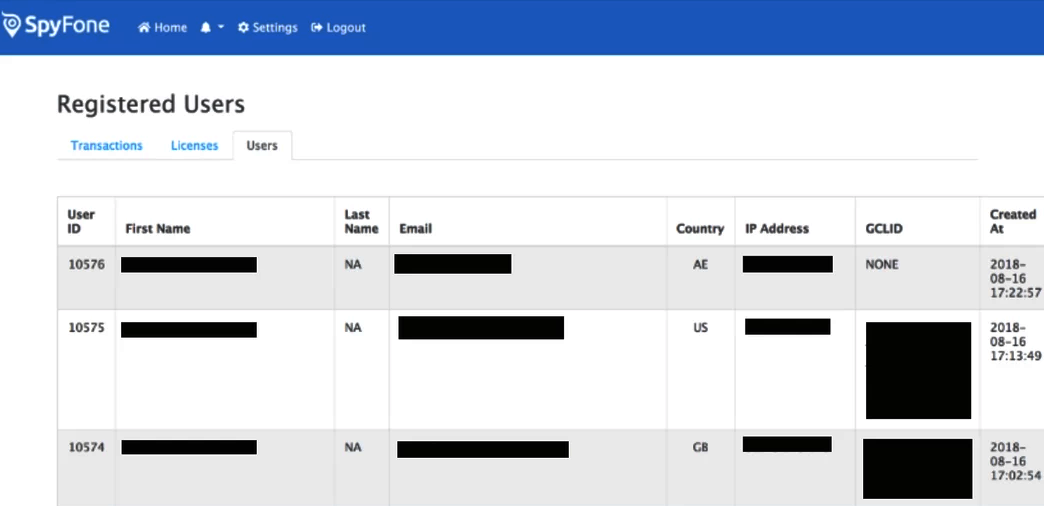
Screenshot of the open SpyFone portal as shared by the researcher. (Source: Motherboard)
Moreover, SpyFone also allowed anyone to view an updated list of customers through an unprotected API merely by guessing the URLs.
“The site shows first and last names, email and IP addresses. As of Thursday, there were more than 11,000 unique email addresses in the database, according to a Motherboard analysis.”
Steve McBroom, a representative of the firm expressed his relief to Motherboard about the timely discovery by the researcher.
“Thank god it is a researcher, someone good trying to protect.”
He also said that the firm is working hard on improvising their site’s security. Moreover, they have also informed the 2,200 affected customers about the breach.

