Morpheus is an open source framework that can launch multiple attacks on the network using applications, such as ettercap, msgsnarf, tcpkill, and urlsnarf. The tool’s main objective is to manipulate the tcp/udp data using these backend applications. Some major tasks that can be performed using the Morepheus framework include https credentials stealing, web browsers traffic sniffing and traffic redirect, buffer overflow attack (using Firefox, Android, and Tor browsers), and cookies capturing. Morpheus uses some pre-configured filters to launch the aforesaid attacks. The filters can be modified as well that are automatically reverted back to default settings at the end of attack.
Morpheus Installation
Morpheus requires apache2, nmap, ettercap, and zenity to operate. The sub-dependencies include sslstrip-0.9, dns2proxy, driftnet, and dsniff. The framework can be installed using the following commands.
git clone https://github.com/r00t-3xp10it/morpheus.git cd morpheus chmod -R +x *.sh chmod -R +x *.py nano settings
How to Use Morpheus
Morpheus interface can be initiated by running the following command.
sudo ./Morpheus.sh
The command loads the Morpheus with a number of attack modules as shown in the following screenshot.
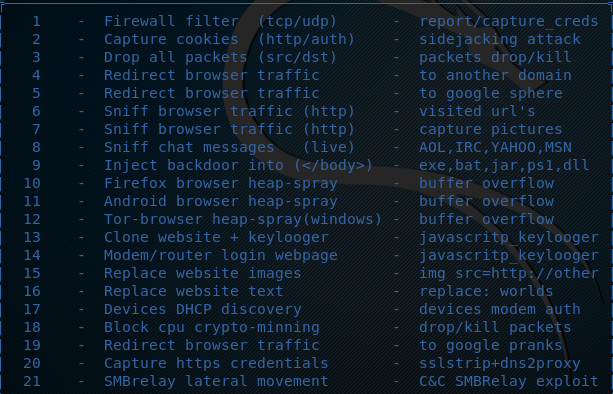
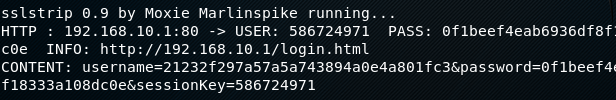
Each module can be initiated by typing its serial number in the terminal.For instance, we can initiate the https credentials stealing module by typing its serial number (i-e 20) in the terminal. This module uses dns spoofing and the man in the middle attack technique to steal the credentials. The module is dependent on sslstrip, ettercap, dns2proxy, python-twisted-web, and iptables to launch the attack. The module first looks if all the dependencies are fulfilled. In the next step, the module asks for the custom ARP poisoning settings to attack a range of the network. With the default settings, the module poisons entire network. Once configured, the module scans the network and starts listening on different ports. If someone in the network logs into a web application using https or http protocol, the module grabs the credentials and displays them on the screen.
Besides offensive security, Morpheus can also be used for scanning purpose. The framework scans the network for the live IP addresses using nmap tool. Morpheus offers different scanning methods, such as normal, stealth, NSE, or target scan.
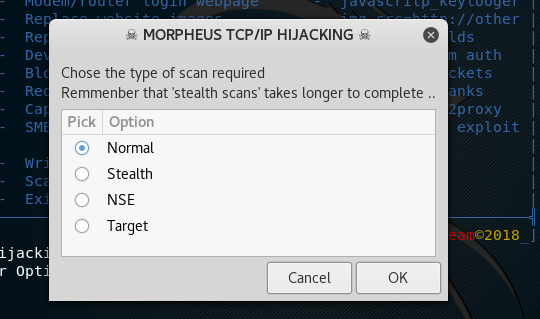
Stealth scan takes a longer period of time as compared to other scans. The target scan option can be used to scan a specific host in the network. All we have to do is just provide the IP address of the target machine and the tool starts scanning the host in the stealth mode.
What Bunny rating does it get?
Morpheus is a decent framework that can launch various network attacks by manipulating the TCP/UDP data. Many attacks performed by the framework are dependent on the success of ARP poisoning. If the network is secure against ARP poisoning or possesses some HTTP Strict Transport Security (HSTS), the Morpheus framework fails in such situations. As a result we will be awarding this tool a rating of 4 out of 5 bunnies.




Want to learn more about ethical hacking?
Do you know of another GitHub related hacking tool?
Get in touch with us via the contact form if you would like us to look at any other GitHub ethical hacking tools.