Yuki Chan is an open source tool that automates some of the information gathering and web application penetration testing process. The tool can automate a number of penetration testing tasks, such as information gathering about the target web application, open source intelligence, and vulnerabilities assessment, CMS information, and system enumeration, SSL security auditing, and fuzzing. Yuki Chan tool is loaded with a large number of modules including Metagoofil, XSS Scanner, DNSRecon, Wafninja, Spaghetti, Joomscan, WPSeku, WPscanner, a2sv, Dirsearch, Whatweb, and sublist3r. Each module runs automatically one after another to scan the target applications.
Yuki Chan Installation Guide
Yuki Chan works only with Linux OS. Besides the preloaded modules mentioned above, Yuki Chan requires the following tools as well to operate.
- Nmap
- SSLScan
- SSLyze
- Wafwoof
- WPScan
These tools can be manually installed if they are not already installed on your Linux system. For example Nmap can be installed using the following command.
apt-get install nmap
Wafwoof can be installed by first cloning the tool using the following path.
git clone https://github.com/EnableSecurity/wafw00f.git
After cloning the tool, move to the wafwoof directory and run the setup file.
cd wafw00f python setup.py install
WPScan and SSLScan can be installed using the following paths.
git clone https://github.com/wpscanteam/wpscan.git git clone https://github.com/ rbsec/sslscan.git
To install SSLyze, use the following commands.
git clone https://github.com/nabla-c0d3/sslyze.git cd sslyze pip install -r requirements.txt --target ./lib
Once the required modules are installed, clone the Yuki Chan tool and complete the installation process using the following commands.
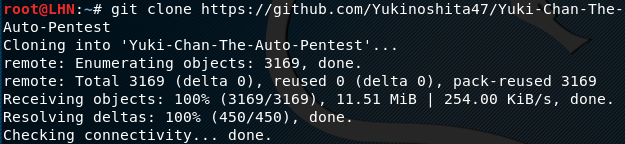
git clone https://github.com/Yukinoshita47/Yuki-Chan-The-Auto-Pentest.git cd Yuki-Chan-The-Auto-Pentest chmod 777 wafninja joomscan install-perl-module.sh yuki.sh chmod 777 Module/WhatWeb/whatweb pip install -r requirements.txt ./install-perl-module.sh
The above commands install the required libraries and scripts to run the tool without any errors.
Yuki Chan Working
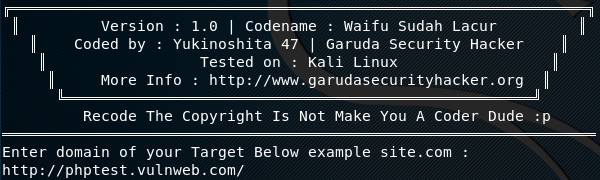
The following command is used to run Yuki Chan.
./yuki.sh
The command not only runs the tool but also prompts for the target host to start scanning and auditing.
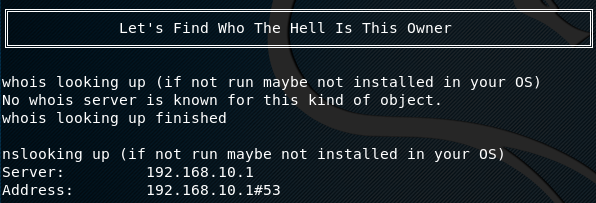
Once the url is provided, the tool automatically loads each module mentioned above to scan the target for reconnaissance and vulnerability assessments. For instance, the tool starts with Whois command to gather owner’s information. It runs DNS tool to gather server information.
Then it starts with the Harvester and the Metagoofil to look for email addresses and the interesting documents.
The other vulnerability assessment tools are automatically executed in a similar fashion to scan the target for possible vulnerabilities or useful information.
What Bunny rating does it get?
Yuki Chan is quite handy for information gathering and scanning the target applications for possible vulnerabilities. However, the tool is more focused on CMS based platforms and not equally efficient against other applications. As a result we will be awarding this tool a rating of 3.5 out of 5 bunnies.



![]()
Want to learn more about ethical hacking?
Do you know of another GitHub related hacking tool?
Get in touch with us via the contact form if you would like us to look at any other GitHub ethical hacking tools.

