The infamous Adwind malware is ready to take on the utilities sector this time. Researchers have discovered a phishing campaign delivering this malware-as-a-service via pdf spoofing.
Phishing Campaign Delivering Malware
Reportedly, the team Cofense has stumbled upon another phishing campaign in the wild. This time, the campaign targets the utilities industry with Adwind malware.
As explained by the researchers in the blog post, the attack begins when a user receives the phishing email. In the malware campaign they noticed, the email came from a hacked Friary Shoes account. It has a brief message with an image file that looks like pdf attachment.
The attached image contains an embedded URL that downloads the payload on the target device when the user clicks on it. This payload looks like a pdf attachment but is actually a .jar file which executes the malware.
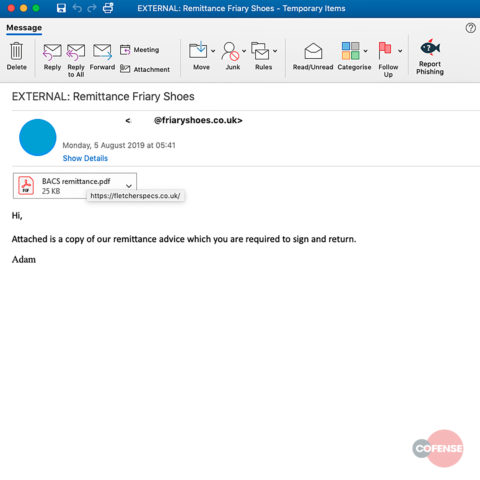
Source: Cofense
About Adwind Malware
The Adwind RAT, also known as JRAT, SockRat, and many other names, has once again made it to the news with this campaign. Previously, it got attention back in 2017 when it targeted more than 1500 organizations in over 100 countries. The malware bears robust malicious properties that make it desirable for the threat actors. It can take screenshots of the target device, access device’s camera and microphone to spy on the user, collect data from the device, and acts as keylogger.
In the campaign discovered, the malware seamlessly reaches the target system via phishing emails. Upon execution, it installs the program in the ‘TEMP’ folder. As explained by the researchers,
Once executed, we can see that two java.exe processes are created which load two separate .class files. JRAT then beacons out to its command and control server: hxxp://ns1648[.]ztomy[.]com
Adwind installs its dependencies and harvested information in: C:\Users\Byte\AppData\Local\Temp\.
The malware also attempts to evade security analysis and detection. It scans the device for the presence of popular antimalware tools and disables it via taskkill.exe. Thus, it becomes difficult to detect and remove from the system.
To stay protected from this malware users must avoid opening such emails from untrusted sources. And even if you open such emails, make sure not to click on any attachments.

