Ransomware attacks have long been a menace for internet users, particularly, the business sector. Despite implementing adequate security practices, various businesses and organizations frequently become a victim of ransomware attacks. Recently, researchers have highlighted how most ransomware can bypass security checks.
Common Ransomware Tactics To Bypass Security
Researchers from SophosLabs have recently published a detailed whitepaper highlighting how most ransomware bypass security measures. They analyzed numerous ransomware variants infamous for their devastating attacks and found numerous tactics that essentially help the ransomware.
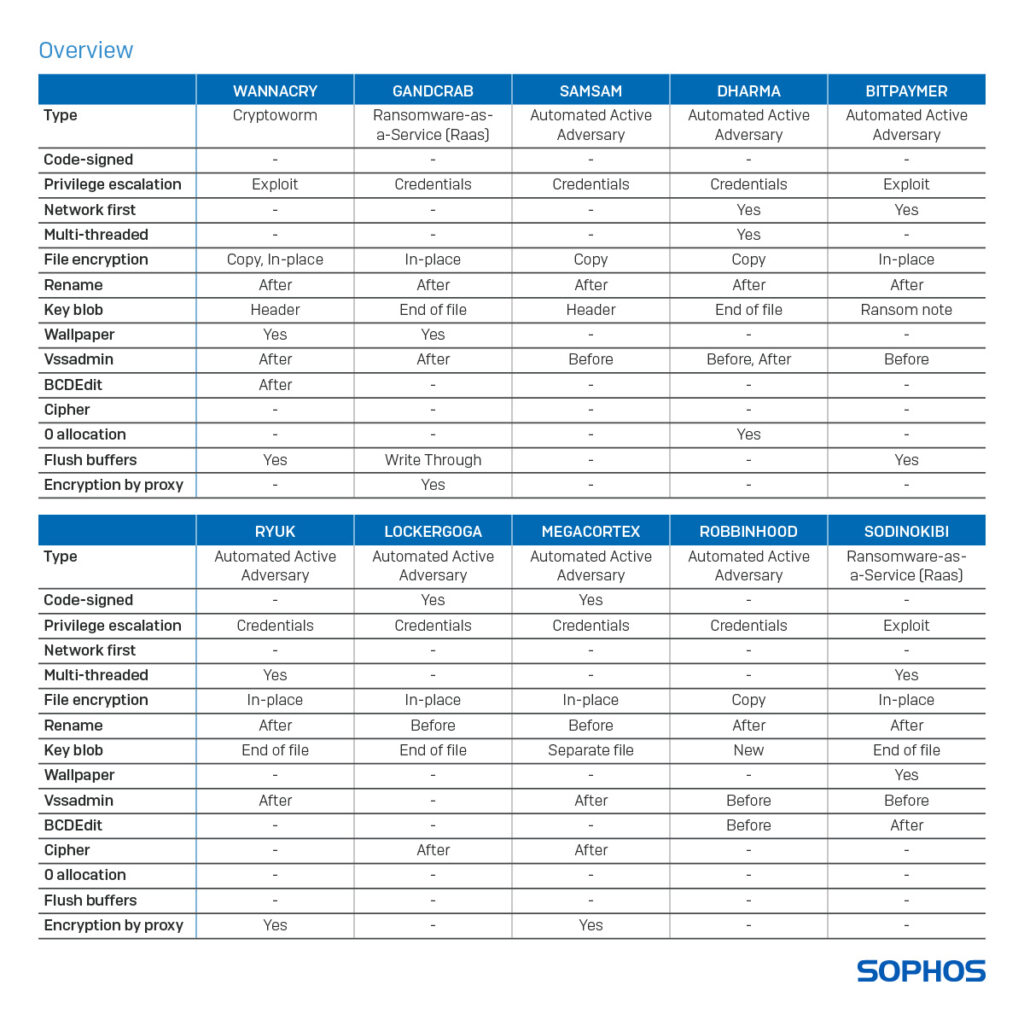
Source: SophosLabs
Here is a quick review of the techniques SophosLabs have highlighted in their research.
Code Signing
A risky, yet viable approach most ransomware apply to bluff security programs is code signing. The attackers sign malicious codes with legit authentication certificates. Thus, they evade all checks from the security tools for unsigned codes.
Privilege Escalation And Lateral Movement
Numerous ransomware exploit various vulnerabilities to bypass restricted accesses. They gain elevated privileges by abusing stolen credentials.
Following privilege escalation, the attackers then disable the defense mechanism of the target device and install a RAT to laterally spread within the system. For instance, they take over the Remote Desktop Protocol (RDP) and destroy any backups to leave no recovery options for the victim.
Network First
Ransomware attacks on businesses often employ the ‘network first’ approach. Since most organizations store business documents across multiple servers connected on a network, the ransomware tends to encrypt the network drives first. This strategy effectively targets the employees, both in-house and remote, of the victim firm, making them unable to work.
Multi-Threaded
Most modern CPUs possess Simultaneous Multithreading (SMT) or Hyper-Threading (HT) technology for better performance. Hence, the attackers also design the ransomware in way to exploit this technology for subsequent faster and more devastating damage to the victim.
File Renaming And Encryption
Ransomware endows damages to the victim by encrypting the files while copying or overwriting them. It then renames the file names to let the user visualize the encrypted, and hijacked data. Whereas, this mechanism also helps the ransomware detect already encrypted files to avoid double encryption. Moreover, this also prevents encryption in case of another ransomware attack.
They have also analyzed some other techniques including change of wallpaper, encryption by proxy, etc.
With this analysis, the researchers believe that IT professionals might get an insight into common tactics by ransomware to design adequate countermeasures.
Let us know your thoughts in the comments.

