Researchers have found symlink race bugs in popular antivirus software. An attacker could easily exploit these vulnerabilities to crash or brick a target system.
Symlink Race Bugs In Antivirus
RACK911 has discovered numerous bugs with underlying symlink race conditions in multiple antivirus software.
Symlink or ‘symbolic link’ is a shortcut to another file allowing underprivileged users to perform in case of macOS and Linux, whilst it isn’t possible for symlinks in Windows it is possible to use directory junctions that link two local directories. These two conditions form the basis of race condition bugs targeting antivirus tools.
According to the researchers’ blog post, these vulnerabilities exist due to the way in which most antivirus work. A standard antivirus tool runs a scan whenever the user saves a file on the hard drive. Upon detecting a malicious or suspicious file, it immediately quarantines the file to stop any potential malware execution.
These scans take place using the highest privileges on the system, just like the file operations in most cases. Hence, due to the time lag between the initial scan and the removal of the malicious file, the malware may execute. As stated in the post:
A malicious local user or malware author is often able to perform a race condition via a directory junction (Windows) or a symlink (Linux & macOS) that leverages the privileged file operations to disable the antivirus software or interfere with the operating system to render it useless, etc.
The researchers observed that exploiting the bugs allowed for deleting of important antivirus files to disable it, and therefore delete important systems files causing a system crash or gain escalated privileges on the target system.
The following videos demonstrate the exploit on Windows (video 1), macOS, and Linux systems (video 2). the detailed explanation of the exploits is also available in the researchers’ post.
The following is the list of vulnerable antivirus programs across Windows, macOS, and Linux.
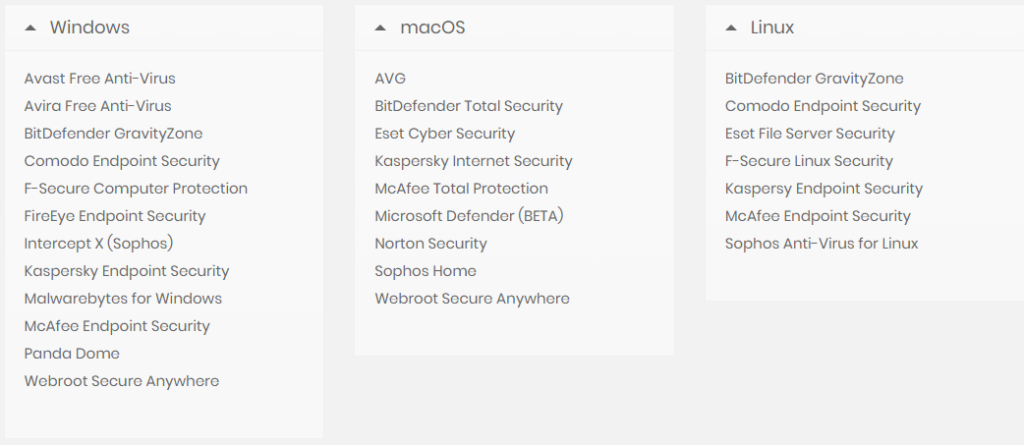
Source: RACK911 Labs
Patches Rolled Out
According to RACK911, successful exploitation of the bugs required extreme precision of timings. An error of even a second could render the bugs unexploitable. However, for an expert adversary, these attacks are pretty easy to execute.
Fortunately, after the researchers notified the antivirus developers, the vendors started fixing the flaws. While most major antivirus are now updated, a few lesser-known tools remain vulnerable. The researchers haven’t named them.



