A security researcher has devised a new browser exploitation technique that can trigger phishing attacks. Dubbed “browser-in-the-browser,” this new attack creates legit-looking browser windows to steal data.
Browser-in-The-Browser (BiTB) Attack
Sharing the details in a post, the researcher with the alias mr.d0x demonstrated the newly-devised browser-in-the-middle attack.
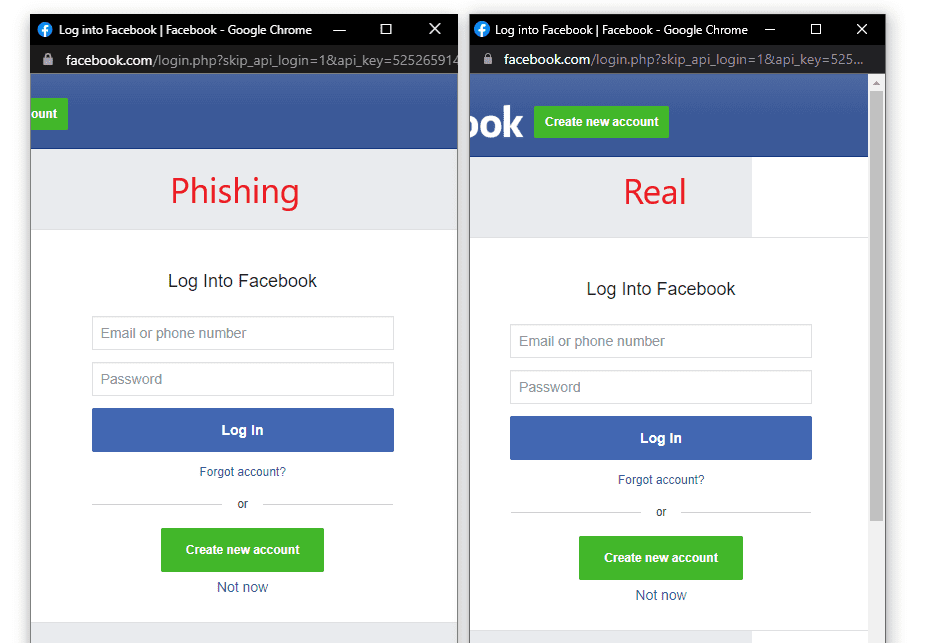
Most services like Google, Microsoft, and more, use the popup window feature to display login pages. As a standard, the users enter their credentials there, and the windows close as the sign-in process continues. Since such windows open separately, the most reliable way to check their authenticity is to observe the URL.
The above is what the researcher exploited as he crafted legit-looking windows via basic HTML/CSS. As stated in his post,
Combine the window design with an iframe pointing to the malicious server hosting the phishing page, and its basically indistinguishable…
JavaScript can be easily used to make the window appear on a link or button click, on the page loading etc. And of course you can make the window appear in a visually appealing manner through animations available in libraries such as JQuery.
With JavaScript enabled, even hovering over the links would not help to check the URL’s legitimacy.
Although, such attacks may not be entirely executable from the attackers’ end, requiring them to land on to the target user’s browser window first. However, once done, it would be trivial for the attacker to lure the victim into submitting login credentials.
In this way, this attack may become a powerful phishing technique for the threat actors.
It currently remains unclear how lucrative this strategy appears to criminals, and how they intend to exploit it in real-world attacks.
Let us know your thoughts in the comments.

1 comment
como puedocer jaker que plicasiom me recomienda
Comments are closed.