While often considered secure, Linux systems are not immune to the ever-evolving threat landscape of malware. Understanding the inner workings of these threats is crucial for effective defense. Let’s explore the world of Linux malware and analyze several examples of it using an interactive sandbox, ANY.RUN.
The State of Linux Malware
Since 2018, there has been a notable increase in the development of new Linux malware variants. This trend is evidenced by the significant jump from 4,706 new variants in March 2017 to 15,762 in March 2018 alone.
According to IBM, in 2020 also, there was a 40% increase in Linux-related malware families, while Go-written malware rose by 500%. This suggests a potential shift in attacker focus towards Linux systems, posing a growing risk to both individual users and organizations alike.
Notable Linux Malware Families
While the overall increase in Linux malware is concerning, understanding the specific families and their capabilities provides valuable insights for effective protection. Here’s a closer look at some notable Linux malware families:
Cloud-Focused Threats:
- CloudSnooper: This malware targets cloud environments, utilizing multifaceted techniques for evasion and persistence. It exploits loopholes in firewall rules to establish covert communication channels and utilizes rootkit capabilities for deep system integration, making it difficult to detect.
Botnets:
- Mirai: This IoT botnet leverages weak security protocols to infect devices and integrate them into a network for large-scale DDoS attacks. Its open-source nature and focus on poorly secured IoT devices amplify its impact.
Ransomware:
- RansomExx: This targeted ransomware strain focuses on enterprises and governments, often delivered through spear-phishing attacks. It appends a unique extension to encrypted files and leverages existing malware like IcedID for initial access.
- GonnaCry: This Python-based ransomware encrypts files and displays a ransom note with payment instructions directly to the user. Its open-source nature raises concerns about potential modifications and wider distribution.
Espionage:
- EvilGnome: Disguised as a legitimate GNOME shell extension, this malware performs keylogging and downloads additional malicious payloads. Its modular design and ability to mimic legitimate processes make it a stealthy tool for targeted espionage.
Multi-Platform Threats:
- Tycoon: This ransomware targets both Windows and Linux systems, using a Java-based format to evade detection. It encrypts files and compresses them into password-protected archives, making recovery efforts difficult.
Beyond these examples, numerous other families and variations exist.
| Button: Analyze Linux malware for free in ANY.RUN, an interactive malware analysis sandbox. |
Analysis of Linux Malware Samples
Suricata Detection of Mirai Activity

Mirai sample analyzed in ANY.RUN
Let’s start with a sample of Mirai. Since it primarily operates through network activity, we can leverage the sandbox’s monitoring capabilities to gain valuable insights. By examining the network traffic generated by Mirai, we can identify specific actions it attempts to perform.
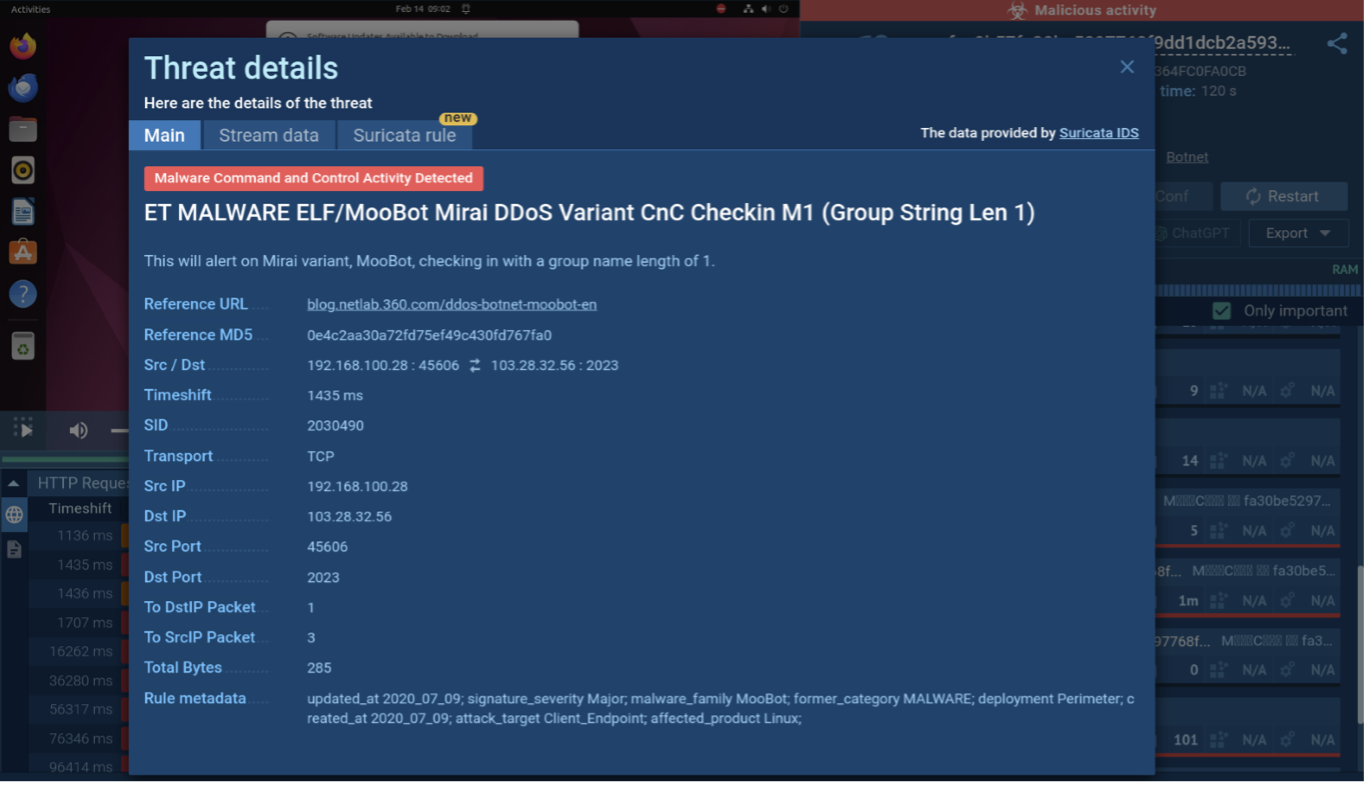
Mirai Suricata rule
As Mirai interacts with the network, it triggers specific Suricata rules. By clicking on the triggered rules, we can access detailed information, including the type of communication, the source and destination addresses, and even the content of the packets themselves.
Cryptominer’s Extensive CPU and RAM Usage
Miners are another common type of malware targeting Linux systems.
Cryptocurrency mining involves solving complex mathematical puzzles which require significant processing power. Hence, after submitting a miner sample for analysis to a sandbox, the CPU usage surges immediately, and a serious RAM drain can be observed.
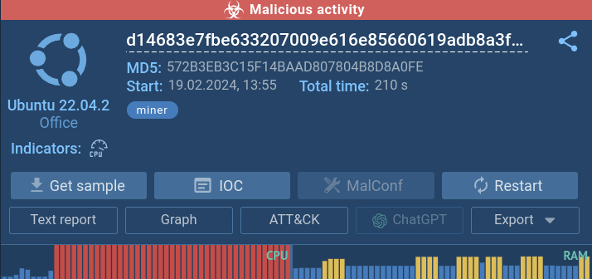
CPU and RAM usage displayed in the sandbox
By uploading a miner sample to a sandbox, its malicious nature becomes evident.
CPU usage spikes almost immediately upon launch, indicating intensive processing activity, while the program also demands significant RAM, further suggesting resource-intensive operations.
Monitoring DDoS Activity of a Botnet
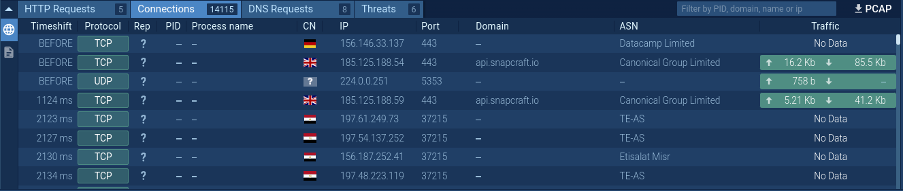
A list of connections made by the botnet
In another example of a Linux botnet, we can observe a large amount of network activity – in one minute, the malware tried to establish a connection over 15,000 times.
Signature-based Detection of Malicious Behavior
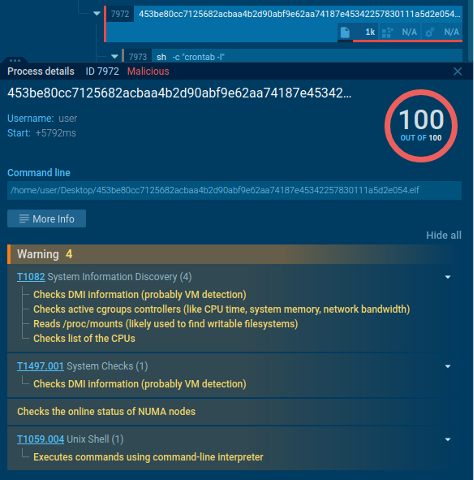
Malicious actions detected by the sandbox
Here is another sample of a miner. The sandbox here uses indicators to detect malicious activity. In this case, the signatures are specific to the miner that is being analyzed. This gives us a better understanding of the miner’s behavior and how it is infecting systems.
Analyze Linux Malware in ANY.RUN
ANY.RUN is a cloud-based sandbox that provides advanced malware analysis capabilities. It lets you investigate Linux malware in Ubuntu 22.04.2 VMs and collect vital threat information on different malware.
Sign up for ANY.RUN at no cost using your business email.

