Once again, the telecommunication sector has been threatened by a major cybersecurity issue. This time, the affectees include several Internet Service Providers (ISPs) from Canada. Reportedly, a vulnerability in the SOLEO IP Relay affected these ISPs as all of them ran the same vulnerable software. However, by applying Soleo’s patch, these ISPs are now safe. (Yet, the story doesn’t end there!)
Security Vulnerability In SOLEO IP Relay Threatened Major Canadian ISPs
Researchers at Project Insecurity have discovered a security flaw in SOLEO IP Relay. They published a detailed white paper about a zero-day vulnerability in the software and informed everyone about it via a tweet.
[VULNERABILITY REPORT/ WHITEPAPER] – SOLEO IP Relay (0day) – Local File Disclosure leading to full system compromise:
Writeup: https://t.co/CU3uVBWJfl#infosec #webhacking #0day #infodisclosure pic.twitter.com/gtvP0rY36O
— PROJECT INSECURITY (@insecurity) August 19, 2018
Reportedly, two researchers, Dominik Penner and Manny Mand, published a detailed vulnerability report lately, in which they explained their findings. The researchers discovered a local file disclosure vulnerability in the TRS (Telecommunications Relay Services), or the IP-Relay powered by Soleo Communications.
As stated in their vulnerability report,
“This vulnerability exists due to the fact that there is improper sanitization on the “page” GET parameter in servlet/IPRelay… A determined attacker (APT/foreign entity) could leverage this vulnerability to steal passwords from configuration files across multiple providers.”
Explaining further about the impact of this vulnerability, the researchers state,
“Within the source code lies passwords which allow the servlet to communicate with other services, such as SQL/LDAP. An attacker could extract these passwords from within the source files, and further escalate their privileges on the server or even use said information in a social engineering attack. The end result could be escalated to yield remote code execution.”
Ip-Relay or TRS enables people with speech and hearing disabilities to make calls through Teletypewriters (TTY) or other assistive devices.
Numerous Canadian ISPs Affected
In their report, the researchers state that they noticed the number of people affected by the vulnerability was constantly increasing. Hence, they analyzed further to reveal the exact list of affected ISPs in Canada.
“By utilizing Google dorks, we were able to determine that there were at least ten other Internet Service Providers in Canada that were running the same vulnerable instance of Soleo’s IP Relay. Interestingly enough six out of the ten vulnerable ISPs were actually the largest telecom providers in Canada.”
Below we share the list of affected Canadian ISPs as listed by the researchers.
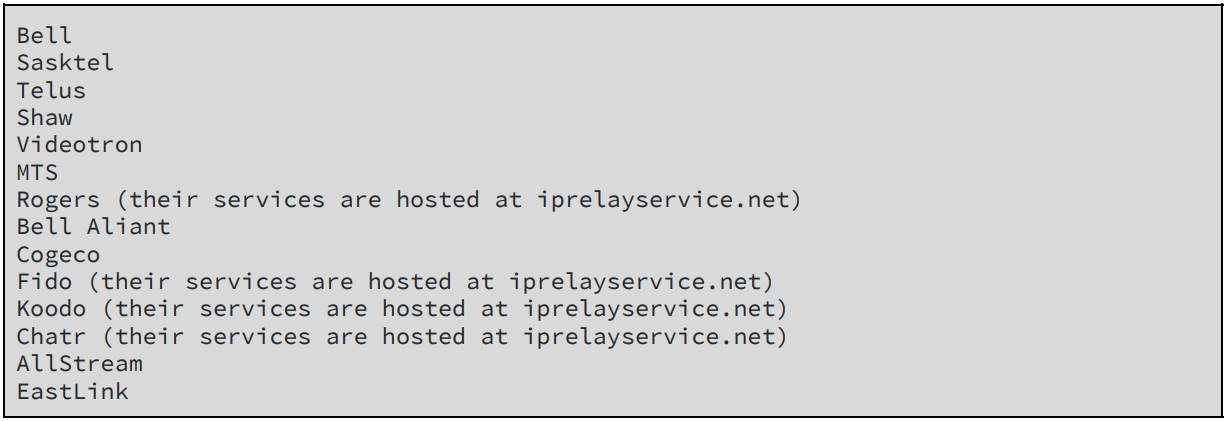
Allegedly, the impact of this vulnerability over the above-listed ISPs could result in a compromise of “30 million Canadian records”. Therefore, the researchers decided to disclose the list keeping in mind the security of Canadian citizens.
Vulnerability Patched – Yet Vendors Refused Disclosure
Researchers reported the vulnerability to SOLEO on July 17, 2018. They sent several emails in subsequent days and even tried to reach a SOLEO official via LinkedIn. Consequently, on August 10, 2018, the vendors confirmed that they have released a patch. Nonetheless, they didn’t confirm any disclosure timeline. As mentioned in their report,
“Vendor confirms patch, refuses to establish disclosure timeline despite multiple attempts.”
Project Insecurity officials say in a tweet that they will publish a blog soon about the report. They will supposedly disclose their reasons for public disclosure of the vulnerability.
All of the major Canadian ISP's have now updated to SOLEO's new patch. This is good. The way disclosure was handled? Not so good. We will blog about this tomorrow to explain the situation in more detail and a few issues that we have.
— PROJECT INSECURITY (@insecurity) August 19, 2018
We shall wait to hear more details about the matter. Especially, the reasoning that made vendors refuse public disclosure. Considering the fact that the vulnerability affected almost all major Canadian telcos, hiding or the intention of hiding such instances from the public sounds suspicious.

