CMSeek is a python tool that is used to detect Content Management System (CMS) within a target website, it can extract useful information like CMS version, installed themes, plugins, usernames, CMS files, and looks for possible vulnerabilities for the identified CMS version. CMSeek can detect more than 130 CMS’s. The CMS detection is performed through HTTP headers, Meta tags, source code, or robots.txt file. The enumeration results are different for different CMS. For example, CMSeek enumerates users, plugins, and theme information for the WordPress CMS. For Joomla, the tool looks for backup files, admin pages, directory listing option, and checks for possible information leakage.
CMSeek Installation
CMSeek is a python3 tool that can be cloned from github using the following path.
git clone https://github.com/Tuhinshubhra/CMSeek
CMSeek requires ‘requests’ and ‘datetime’ packages, mentioned in the requirements.txt file. The requirements can be installed by running the following commands.
cd CMSeek pip install –r requirements.txt (or pip3 install –r requirements.txt)
Using CMSeek
CMSeek can be set into action by running the cmseek.py file using the following command.
python cmseek.py
The above command sets the tool into an interactive mode with multiple options on the screen, such as CMS detection and deep scanning, bruteforcing CMSs, scanning multiple targets in a single run, and rebuilding the cache in case of adding custom modules to the CMSeek directory.

We can select any of the available options. For instance, by picking the first option, i-e CMS detection and deep scanning, the tool asks for the target website to start scanning. Once the target url is provided, the tool searches for the CMS. If the CMS is a WordPress website, the tool looks for the CMS version, enumerates plugins and themes information, and tries to harvest the usernames associated with the target website.
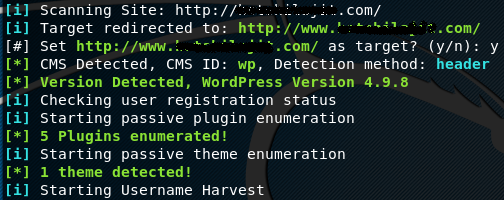
CMSeek looks for user information in wp-json api, jetpack public api, and author parameters.
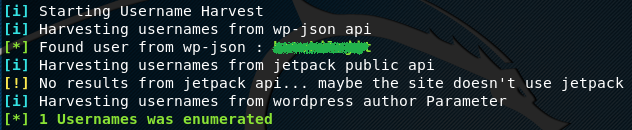
During the deep scan process, CMSeek also looks for readme file, license file, and Change log file. The plugins found during the scan are enumerated according to their names, versions, and upload path.
What Bunny rating does it get?
CMSeek is a nice little tool that can find some quick information about a website. CMS, themes, and plugin information is vital in identifying associated vulnerabilities. Similarly, the usernames identification feature helps in analyzing the possibility of bruteforce and dictionary attacks. However, the vulnerability assessment feature of the tool is very ordinary. The tool is only good for information gathering. As a result we will be awarding this tool a rating of 3.5 out of 5 bunnies.



![]()
Want to learn more about ethical hacking?
Do you know of another GitHub related hacking tool?
Get in touch with us via the contact form if you would like us to look at any other GitHub ethical hacking tools.

