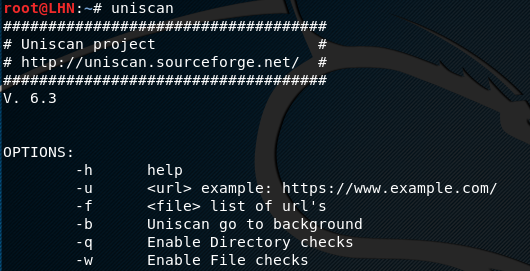
Uniscan is an open source tool capable of scanning web applications for critical vulnerabilities, such as sql injection, blind sql injection, cross site scripting, remote file inclusion, web shell vulnerabilities, hidden backdoors, amongst others. Besides vulnerability assessment, Uniscan can also do a Bing and Google search for finding domains on shared IP addresses.
Uniscan Installation
Uniscan is a Perl tool that can be installed by running the following command in Linux terminal.
sudo apt-get install uniscan
The command installs Uniscan tool along with its dependencies. Alternatively, we can also clone Uniscan from github using the following path.
git clone https://github.com/poerschke/Uniscan
Uniscan Vulnerabilities Assessment
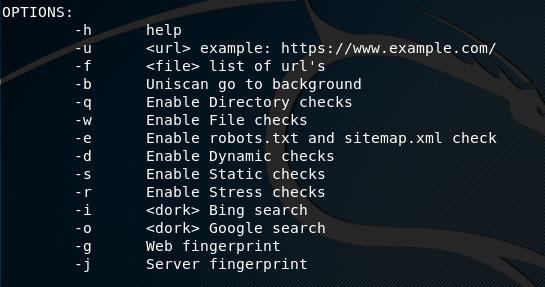
Uniscan comes with two major scanning options i-e (i) dynamic search and (ii) individual search. In dynamic search, the tool looks for all the possible vulnerabilities in the target web application. In individual search, different options can be used to achieve individual goals like web fingerprinting, server fingerprinting etc. The complete list of options can be seen in the following screenshot.
Dynamic search is the most comprehensive option in Uniscan. The following command can be used to do the dynamic search of the target domain.
uniscan -u http://testphp.vulnweb.com/listproducts.php?cat=4 -d
The tool loads all the available plugins to perform a comprehensive analysis of the target web application. The tool crawls the urls of the target domain and checks for possible vulnerabilities, such as backdoors, SQL injections, blind SQL injections, Cross Site Scripting, Remote command execution, Remote file inclusion, web shells, directories, and source code disclosure. If any vulnerable urls are found, they are displayed on the screen as shown in the following screenshot.
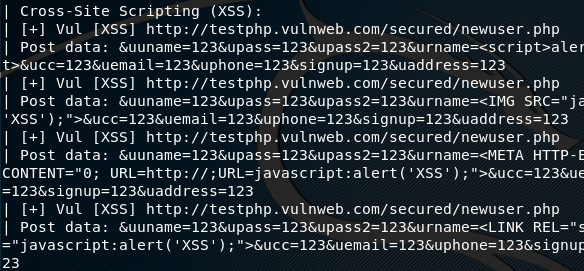
Uniscan can also be used for scanning the web applications for specific vulnerabilities/goals using the available options. The optional flags are appended with the scanning command in the following way.
uniscan –u <target web application> -<available option>
For instance, the following command can be used to do the web fingerprinting,.
uniscan -u http://testphp.vulnweb.com/listproducts.php?cat=4 -g
Uniscan web fingerprinting fetches hosting server information, installed plugins and modules, web services, Whois information, and some interesting strings.
Similarly, -j flag can be used to do the server fingerprinting of the web application.
uniscan -u http://testphp.vulnweb.com/listproducts.php?cat=4 -j
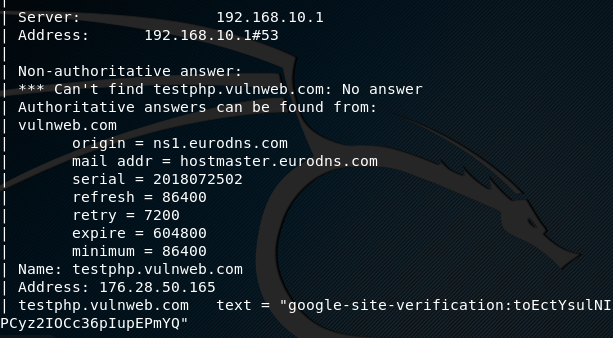
Uniscan performs pings and trace route operations to get information about the server. The type of information that is extracted during the scan includes server type, server version, server IP addresses, server origin, mailing addresses etc.
What Bunny rating does it get?
Uniscan is capable of finding the critical web application vulnerabilities. The tool can be used for cross verifying vulnerabilities found using other penetration testing frameworks. The best feature of the tool is the ability of finding additional vulnerable urls beside the one that is fed into the tool for scanning purpose. The tool however becomes slow while crawling a large number of urls in the target web applications. As a result we will be awarding this tool a rating of 4 out of 5 bunnies.




Want to learn more about ethical hacking?
Do you know of another GitHub related hacking tool?
Get in touch with us via the contact form if you would like us to look at any other GitHub ethical hacking tools.