Telegram has become increasingly popular worldwide due to its secure nature. The provision of encrypted conversations, both in texts as well as calls, makes it desirable for everyone. While the app flaunts its secure environment, recently, a researcher discovered a glitch that leaked IP addresses in Telegram’s desktop client. After being notified of the problem, Telegram patched IP address leak flaw.
An IP Address Leak Bug Discovered In Telegram Desktop Client
Security researcher, Dhiraj Mishra, discovered a glitch in the configuration of Telegram desktop client that caused an IP address leak. The researcher found that the bug allegedly leaked IP addresses while making calls with the desktop app.
According to Mishra’s discovery, the IP address leak problem exists in the Telegram Desktop clients, tdesktop and Telegram for Windows. As stated by the researcher,
“Strangely tdesktop 1.3.14 and Telegram for windows (3.3.0.0 WP8.1) leaks end user private and public IP address while making calls. “
Telegram allows the users to make calls over P2P. While doing so, users can modify the settings to control their IP addresses leak by choosing “nobody” or “never” in the “Peer-to-Peer” settings.
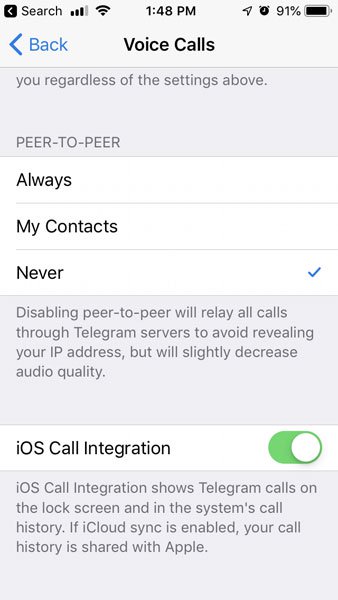
Settings for P2P in the Telegram iOS app. (Source: Bleeping Computer)
These settings are available only in case of the mobile (Android and iOS) apps, and not in the desktop clients. Thus, users making calls via desktop apps inadvertently exposed their IP addresses.
While talking to Bleeping Computer, Mishra explained,
“If you see in my video PoC there are 3 IP’s that leak: 1. Telegram server IP (That’s Ok) 2. Your own IP (Even that’s okay too) 3. End user IP (That’s not okay)”
Telegram Patched IP Address Leak Bug
The vulnerability existed in the Telegram desktop apps tdesktop v.1.3.14 and Telegram for Windows v.3.3.0.0 WP8.1. After discovering the flaw, Telegram patched the IP address leak glitch in the latest versions 1.3.17 beta and v1.4.0 by introducing the “Nobody” option in the P2P settings. Telegram confirmed the patch while replying to Mishra’s tweet.
Sorry, this is misleading people. The default setting is and was "My Contacts". The main apps used for calls – iOS, Android – always had it on. Only Telegram Desktop had a bug which is now fixed thanks to your report.
— Telegram Messenger (@telegram) September 29, 2018
The vulnerability discovered by Mishra received CVE number CVE-2018-17780, he was awarded a bounty of €2000.
Users can simply protect themselves from such accidental IP leaks via Telegram by making sure that their apps’ P2P setting is set to “My Contacts” or “Nobody”/”Never”. This can be done via the following settings menu.
Settings > Privacy and security > Calls > Peer-to-Peer