Galileo is a free web application auditing framework that can perform various penetration testing tasks, such as information gathering, fingerprinting, bruteforcing, injection test, and exploiting vulnerabilities. Galileo uses different modules to perform these tasks. The modules can be divided into following categories.
- Bruteforce
- Disclosure
- Fingerprint
- Injection
- Scanner
- Tools
- Exploitation
Bruteforce modules can be used to bruteforce the credentials. Disclosure modules can find information like credit card data, private IPs, emails, and source code. Fingerprinting modules can gather information about Content Management System (CMS), frameworks, and servers. Injection modules can check the OS command and SQL injection vulnerabilities in the target web application. Exploitation module can exploit the errors like shellshock vulnerabilities.
Galileo Installation
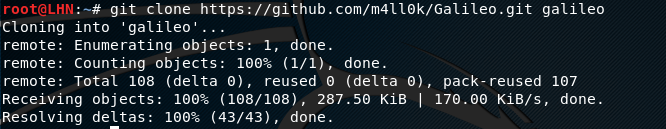
Galileo can be cloned from Github repository as follows.
git clone https://github.com/m4ll0k/Galileo.git galileo
To install the requirements, follow the following commands.
cd galileo
python2 -m pip install -r requirements.txt
Galileo Working
To run Galileo, simply type the following command in the terminal.
python2 galileo.py
The command loads list of modules categories, as shown in the following screenshot.

In order to view list of modules, use the following command.
show modules
To use the desired module, type its name in the following format.
use <module name>
For example, to use fingerprint/server module, type the following command.
use fingerprint/server
In order to define the target web application, we need to use the set parameters. The available set parameters can be seen by typing set help command in the terminal.
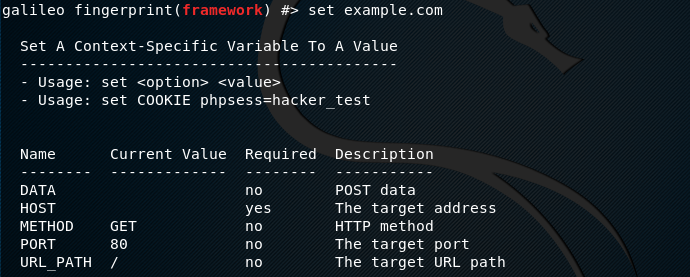
To define the target web application, we need to use set HOST parameter in the following format.
set HOST <target web application>
To execute the selected module, simply type run in the command line.
run
The module runs and displays the results on the screen as shown below.
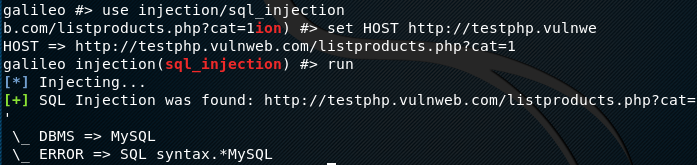
We can use all the modules in the same way. For instance, to use the SQL injection, we can use the injection/sq_injection module in the following format
use injection/sql_injection set HOST <target web application> run
If the target web application is vulnerable, the module responds with the backend Database Management System (DBMS) information.
What Bunny rating does it get?
Galileo is a simple tool that can perform active and passive security tests. Besides Information gathering and vulnerability analysis, Galileo can be used to exploit the vulnerabilities. However, the scope of vulnerabilities analysis and exploitation is limited. So for this I give it 3 out of 5 bunnies.



Want to learn more about ethical hacking?
Do you know of another GitHub related hacking tool?
Get in touch with us via the contact form if you would like us to look at any other GitHub ethical hacking tools.

