Spotify users have to become cautious due to another round of a Spotify phishing campaigns that targets users’ credentials. The campaign employs typical phishing tactics – that is – enticing users to click on malicious links via email. It appears somewhat trivial owing to the many loopholes in it that can alert an avid user of false claims the emails use
Spotify Phishing Campaign Targeted At Login Credentials
Researchers from the cybersecurity firm AppRiver have discovered a phishing campaign specifically targeting Spotify users. The attack method includes an attractive Spotify promotion service to lure the targeted users to click on malicious links via emails. Once done, the malicious page asks the victim to enter his/her login credentials that of course are transmitted to the attackers.
The researchers have explained their discovery of this Spotify phishing campaign in their blog post. As explained in their report, the phishing email asked users to click on a given link to confirm their Spotify account in order to remove any restrictions.
“In this instance, the attacker wants the unsuspecting user to click on a green button with the words “CONFIRM ACCOUNT.” Just above the button, the hacker attempts to lure them in further by urging the user to confirm their account to remove restrictions on the account.”

Source: AppRiver
Upon clicking the green button, the user sees a new window with a login page. This malicious site looks quite similar to the legit Spotify login site to confuse the victims.
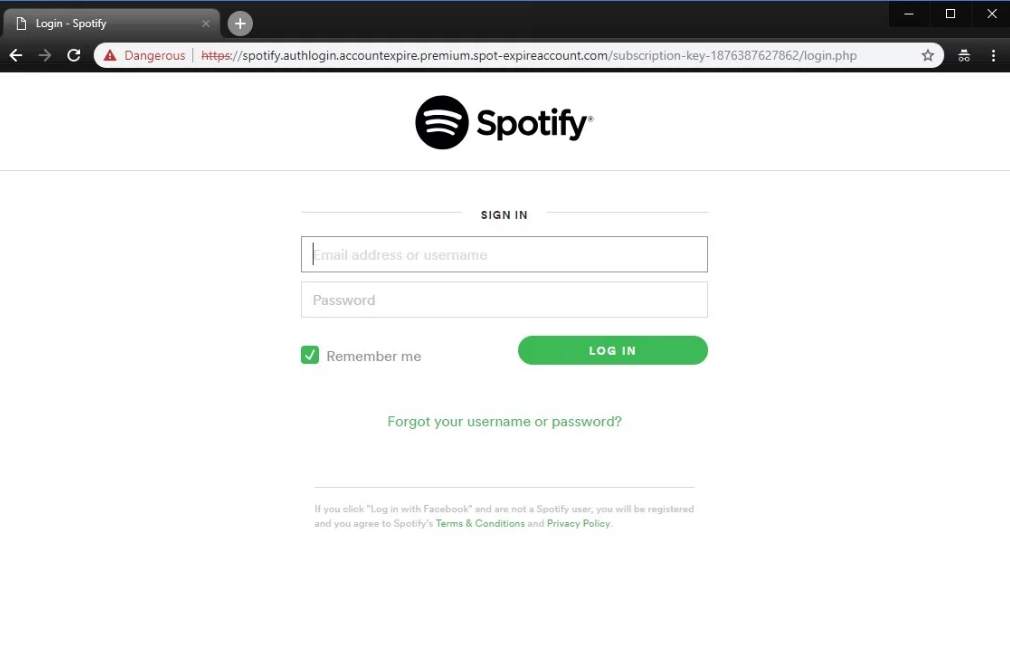
Source: AppRiver
At this point, as the victim enters their login credentials, he/she loses the account details to the attacker.
Loopholes In The Attack Method
Like any other phishing attack, the hackers have tried to imitate Spotify websites to look legit. However, they missed certain things that can let the victim identify this attack. As explained by the researchers,
“The first clue this is a phishing attempt is in the From Address of the email. The From Address domain is not from Spotify.”
It seems the attackers forgot to spoof the sender’s email address. Nonetheless, even they do now, the researchers have pointed out some other identification marks.
“…hover your mouse over the clickable button to see the destination link. In this case, you notice the link is not taking you to an official Spotify page. This URL will redirect you to a deceptive website.”
In case a user clicks on the green button, a quick look at the URL in the browser’s address bar will indicate the issue.
To stay protected from such attacks, the users should always scrutinize incoming emails, particularly those asking for login details or other sensitive information. The AppRiver researchers also recommend checking the sender’s email address before trusting an email. Besides, they also recommend checking out links first by hovering the mouse on clickable buttons, before actually clicking on them.
Take your time to comment on this article.

