A researcher has found a new attack method that can extract BitLocker encryption keys. As a result, the attack puts the security of the stored data on target laptops at risk of hacking. This attack method requires physical access to the target device.
Extracting BitLocker Encryption Keys
According to a report by Denis Andzakovic from Pulse Security, the researcher has found a new attack method that can compromise BitLocker encryption keys. The attack method requires physical access from the attacker. Using this technique, the attacker can decrypt the drive and access stored data.
As stated in his report about the findings,
“You can sniff BitLocker keys in the default config, from either a TPM1.2 or TPM2.0 device, using a dirt cheap FPGA and now publicly available code, or with a sufficiently fancy logic analyzer. After sniffing, you can decrypt the drive”
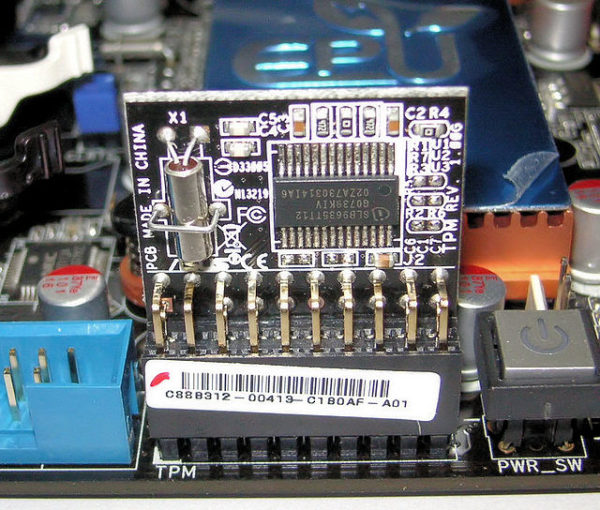
Reportedly, he could extract encryption keys from the Trusted Platform Module (TPM) chip of the target computer by hard wiring the motherboard through a field programming gate array. He tested his findings against two different devices – a HP laptop featuring a TPM1.2 chip, and a Surface Pro 3 with TPM2.0 chip.
“When you enable BitLocker in its default configuration, no additional user interaction is required at boot. This is due to the TPM only being used to decrypt the VMK… As the decryption happens automatically, if we can sniff the VMK as its being returned by the TPM then we can enter that information into any number of BitLocker libraries and decrypt the drive.”
Possible Mitigation
As a possible mitigation, researchers have suggested using a PIN at the boot stage.
“Enabling BitLocker with a TPM+PIN protector should mitigate this vulnerability, however, user’s will be required to enter a PIN at boot.”
In addition, he also mentioned about using smart cards or USB security keys as pre-boot authentication methods.
In response to his report, Microsoft stated that the phenomenon is common in dTPMs, both 1.2 and 2.0. Besides, they also recommended using pre-boot authentication.