Every reconnaissance phase has a standard checklist that is to be followed. If you’ve ever conducted or been a part of target recon you’ve most likely encountered, these steps:
- Network Scanning
- Directory Brute forcing
- Subdomain Brute forcing
- Target Mapping
Today, we’ll be focusing on the the 2nd and 3rd contenders, with an awesome utility written by OJ, in Golang. A weird choice in my opinion but a wonderful product none the less.
What is Gobuster?
Gobuster is a URI and Subdomain brute forcing tool, which in the simplest terms possible means that the tools makes a request asking for a File or a Directory on the server, depending on the server’s response it determines whether the file or directory exists or not.
This can yield some serious results in the form of sensitive file exposure, which in turn can widen your target scope for both recon and exploitation. Now that I have done a wonderful job of selling you the idea to learn Gobuster, let’s install it on our machines.
Installing Gobuster
There are two ways you can obtain Gobuster, through the APT repository or compiling it manually through Git. I highly recommend the second approach if you’re planing to punish you for your past sins.
- Installing Through Git
- Installing Through APT
APT Method
To install gobuster simply write the following on your terminal
sudo apt update && sudo apt upgrade -y sudo apt install gobuster
Here through our first line of code, we’re updating our systems so that we have the latest stable build of all the dependencies that your system may require for installing Gobuster.
Then we simply fetch Gobuster from the APT repositories.
Compiling through GIT
If you want to get your hands dirty you can try the manual compilation approach.The first thing we need to do is get the clone the Git repository onto our local machine.
git clone https://github.com/OJ/gobuster
This command will download all the files from Git onto your machine. As previously mentioned Gobuster is written in Golang which means we’ll need to acquire it as well.
sudo apt install golang
The following command will download, install and setup the Golang environment on your system, if it isn’t already done. Once completed, navigate to the Gobuster directory and begin the compilation process.
Gobuster has external dependencies hence the first step would be to acquire those through the following command
go get && go build
This command will fetch all the dependencies and build a binary for you which you can execute. To add this to your Golang Path so that you can call it from anywhere in your shell, use the following command
go install
Nice, now that we are finally done installing Gobuster let’s get to using it.
Gobuster Usage
To start the most basic bruteforce on your target, you can try the following flags
gobuster -u https://target.com -w /usr/share/wordlist/dirb/common.txt
We’re calling the Gobuster binary and supplying the following flags, -u is for supplying the URL of our target and -w is for giving the wordlist gobuster can use to traverse through the directories and files.
Note- Here, a wordlist is a collection of names of sensitive files, found most commonly on different servers, frameworks and environments. You'll already have a wordlist if you're Kali or Parrot OS in the same directory as mentioned in the aforementioned command.
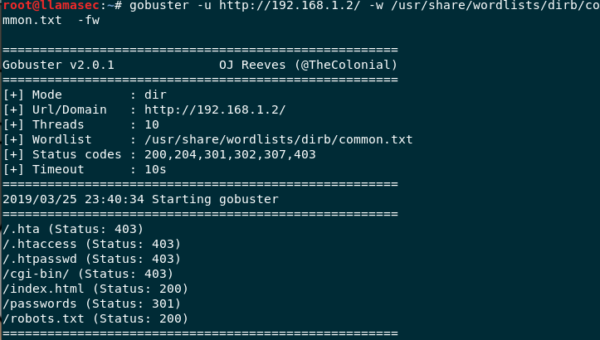
This command will generate an output like this
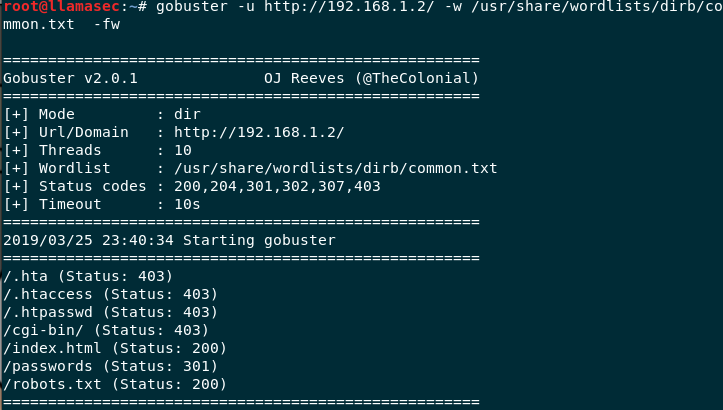
Gobuster output
You can clearly see that we find a lot of interesting stuff by a simple URI bruteforce.
Note - This is not a real world target but a CTF box (stay tuned for a writeup), and you may not find passwords directory just lying around but you can very well find some more interesting stuff which may reveal the stack that the target may be running.
Save Gobuster Output
It’s neat that Gobuster provides us with such a friendly, human readable output, but in the long run you’d most likely want to save it in a file. To do that we can use the following flag
gobuster -u https://target.com -w /usr/share/wordlist/dirb/common.txt -o output.txt
The -o flag will generate an output file called output.txt, but you can obviously name it whatever you want.
Final Thoughts
Gobuster is an essential tool for performing Recon, the fact that it’s written in Go does damage it’s extensibility cause there aren’t a lot of popular wrappers around Golang for different programming languages to interact with it, but the batteries that do come included inside the box are good enough for most. Gobuster ships with Subdomain enumeration as well, and if you’re dealing with only a single target, it’s good enough, but as soon as your scope reaches past 3 or 4 targets, you may want to opt for something like Massdns. Overall I would rate it 4 as it provides a light weight CLI interface for interacting and is not a heavy and clunky directory enumerator like Dirbuster.




Want to learn more about ethical hacking?
Do you know of another GitHub related hacking tool?
Get in touch with us via the contact form if you would like us to look at any other GitHub ethical hacking tools.