Photon is a relatively fast crawler designed for automating OSINT (Open Source Intelligence) with a simple interface and tons of customization options. It’s designed by S0md3v and is written in one of my most favorite language, Python. Photon essentially acts as a web crawler which is able to extract URLs with parameters, also able to fuzz them, Secret AUTH keys and a lot more.
Installing Photon
It’s fairly easy to install Photon all you have to do is clone the Github repository from here, install the dependencies, and run the script.
git clone https://github.com/s0md3v/photon.git
Installing Dependencies
Installing dependencies in Python is pretty easy, most developers place a requirements.txt file along with their package which has a list of all the dependencies with the specific version being used in the script. So time to CD into the cloned repository and install the dependencies.
cd Photon python3 -m pip install -r requirements.txt
Here we call the python3 binary and run the module pip which is a package manager for Python through command line. Later we pass the flag -r to PIP for passing a list of requirements in it. PIP will go line by line and install all the packages required. I already have the packages installed so this is what I get, your output may differ.
PIP output
Photon in action
Now that are environment is all setup it’s time to startup Photon.
python3 photon.py
If everything went well this is the output you’ll get.
Photon output
As you can see Photon offers a lot of options for you to play with. You can crawl a single website, clone the website, set link depth, specify user agents, and obviously a Lot more.
Crawling a Website
We’re going to start simple and crawl a single website right now.
python3 photon.py -u "https://llamasec.tk"
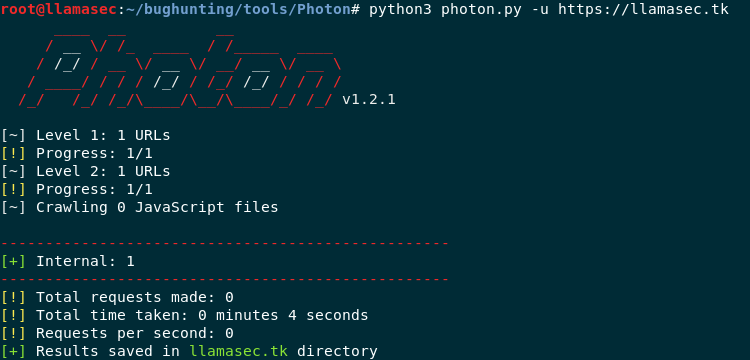
Photon in action
Note - Do NOT run your scans on llamasec unless authorized to do so.
The output gets stored in llamasec directory with a file called internal.txt. There isn’t much there but then again the website is quite static. Let’s try something which is more dynamic with extra set of options this time.
Photon with Options
Tesla has an open bug bounty program so we’re going to scan them for now.
python3 photon.py -u "https://www.tesla.com/" -l 1 -t 10 -o sorryElon --dns
Here we ask Photon to scan Tesla, with a dept scan level 1 and 10 threads, also we’re specifying the output directory to sorryElon, with DNS mapping as well.
This time Photon will scan for multiple javascript files and store it in the output along with a list of all the subdomains associated with that domain. One thing to note here is that the scan timing was pretty quick and much better than other tools. S0md3v also went the extra mile to add a visual DNS map which is a great touch.
What Bunny Rating Does it Get?
My experience with Photon is a mixed one. I have used it for weeks and it’s been pretty useful for me specially with the ability to fetch URLs from the Wayback machine, which widens the scope massively. The only issues I have with the tool are minor ones, such as the output in internals.txt isn’t UTF-8 encoded, it could be a Python3 thing but it still bothers me. Over all I would give it a solid 3 out of 5 bunnies.



Want to learn more about ethical hacking?
Do you know of another GitHub related hacking tool?
Get in touch with us via the contact form if you would like us to look at any other GitHub ethical hacking tools.

