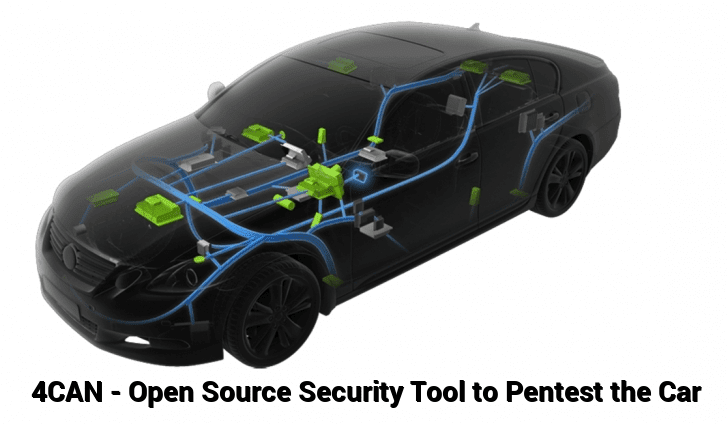
4CAN V2 is a Raspberry Pi project created by the Cisco team in order to test the security of cars via the 4CAN bus, it can also send random payloads to automate this process.
Background
In the last decade, companies release modern cars that are connected to certain networking gateways with limited protection, we sometimes see in the movies peoples cars being hacked remotely which looks far fetched, but is sadly now a reality. Cisco released an open-source tool called 4 CAN to help test for vulnerabilities on modern cars.
Installation
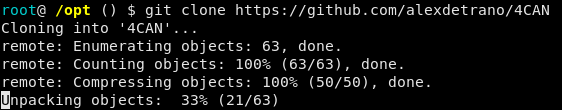
1 – git clone https://github.com/alexdetrano/4CAN
2 – cd 4CAN and run ./install.sh
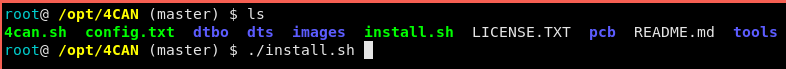
3 – The installer will do these tasks
3.1 – Copy the 4 mcp2515-canx.dtbo files to the directory /boot/overlays

3.2 Making a backup for the original /boot/config.txt (In case …)

Usage
1 – Plug your Raspberry Pi

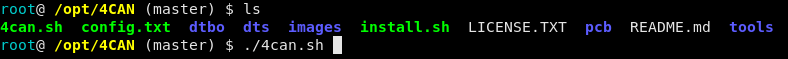
2 – Run ./4CAN.sh
What Bunny Rating Does it Get?
4CAN V2 Raspberry Pi is a fully automated tool when it comes to testing the security of a car, the tool runs as a bash script which is about as convenient as it can get.
PROS
– Fully automated
– 4Can Bus compatible
Cons
– Whilst automated it still requires some expertise to use




Want To Learn More About Ethical Hacking?
Do you know of another GitHub related hacking tool?
Get in touch with us via the contact form if you would like us to look at any other GitHub ethical hacking tools.