What is Infection Monkey?
Infection Monkey is an open-source breach and attack simulation tool for testing a data center’s resiliency to perimeter breaches and internal server infection. Infection Monkey will help you validate existing security solutions and will provide a view of the internal network from an attacker’s perspective.
It is one of the first security tools to operate on a zero trust framework and can self propagate over a data center’s network and reports back to a centralized server. It is made up of two separate parts- the monkey is the tool that infects the machines, and the monkey island is the dedicated server that the monkeys report to.
How does it work?
The monkey uses predefined passwords, common logical exploits and mimikatz to propagate across a data center. Some of the exploit methods used target SSH, SMB, WMI, Shellshock and more. Infection Monkey can be run on multiple platforms including Windows, Docker, Linux and more. For more information on exploits visit the link below.
https://www.guardicore.com/infectionmonkey/docs/reference/exploiters/
Setup is a breeze in Windows all you need to do is download and launch the desktop icon then verify your signed certificate. Once you are setup you will be asked to create an account, this account will be used to access the Island. You will then navigate to the Island IP on port 5000 and sign in. Next select run monkey and let it go to work.
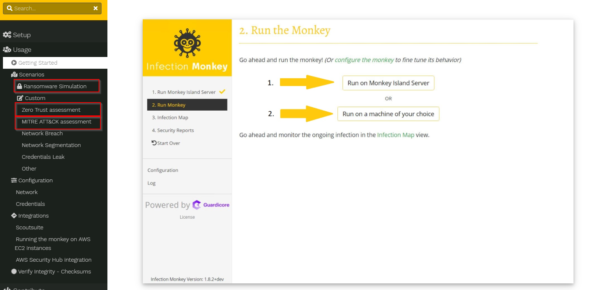
Infection Monkey can run ransomware simulations, zero trust assessments, and ATT&CK assessments as well as detect for network breaches and credentials leaks. It can also be run on the Monkey Island server or on a specific machine of your choice making this tool even more compatible. Here are some screen shots from GitHub

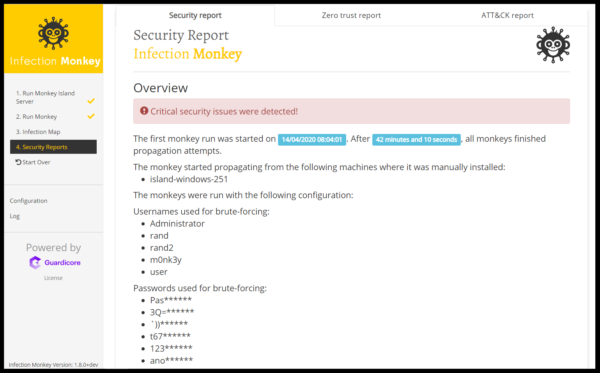
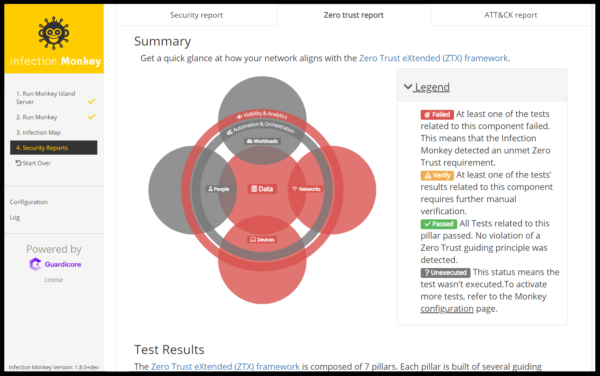

Conclusion:
This tool is marketed towards data center’s but I can’t seem to find a reason why even a small enterprise wouldn’t find this tool very useful. It can run on almost any platform, its entirely free under a GPLv3 license and has a substantial amount of useful tools that can help protect any network. This one is going to take the bar at a 4 out of 5 bunnies on my scale!




Want to learn more about ethical hacking?
We have a networking hacking course that is of a similar level to OSCP, get an exclusive discount here
Help support LHN by buying a T-shirt or a mug?
Check out our selection here
Do you know of another GitHub related hacking tool?
Get in touch with us via the contact form if you would like us to look at any other GitHub ethical hacking tools.

