Reconnaissance is one of the first steps to conduct within a pen test engagement. During this stage, information is gathered using different tools and sources. Some web applications may hide web resources from public, there is however a way to discover the hidden content. Cansina is one such open source tool that helps aid in discovering hidden content using a request and response method.
How do I install this tool?
Cansina can be installed by copying the setup from github repository. we do however also need to install the dependencies to ensure the tool works properly. The tool and dependencies can be installed using the following commands:
pip install --user requests[security] git clone --depth=1 https://github.com/deibit/cansina
Content Discovery Using Cansina

Cansina provides different options (commands) to discover the content on the target website. We can use the following command to discover content on the target web application.
python cansina.py –u <target website> -R
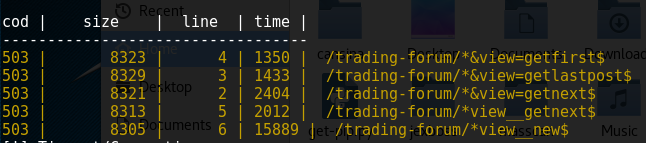
The aforementioned command scans for hidden content. The tool looks for robots.txt file on the target webserver to use it as a payload. The output (discovered content) is displayed in a tabular format. By default, server response codes and file sizes are recorded for the discovered content.
we can skip the server response codes if required. Additionally, we can use a custom payload to discover content on the target website using the following command:
cansina.py -u <target_url> -p <payload_filename> -b 400,500
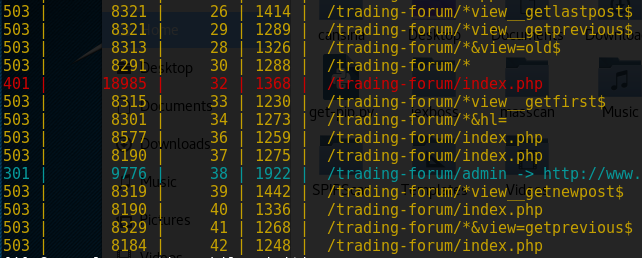
The above command uses a custom payload and skips the 400,500 http server responses.
We can narrow down the discovery process to direct the tool to look for specific content using the following command.
cansina.py -u <target_url> -p <payload_filename> -c <look_for_this_content>
Similarly, we can skip specific file sizes (say for example 500) to filter the content using the following command. We can also provide a list of sizes to skip them in the search result.
cansina.py -u <target_url> -s 500 -p <payload_filename>
Cansina Features
– Cansina supports multithreading and multi-extension search process.
– The tool offers multiple options to filter the content discovery.
– SSL and proxy support is available for the tool.
– Cansina stores the output in sqlite database for easy data management.
What Bunny rating does it get?
Cansina is a fantastic, easy to use tool that helps discover web based content that could be leveraged within a pen test for later exploitation . As a result we have decided to give this tool an awesome rating of 3.5 out of 5 bunnies.



![]()
Want to learn more about ethical hacking?
We have a networking hacking course that is of a similar level to OSCP, get an exclusive 95% discount HERE
Do you know of another GitHub related hacking tool?
Get in touch with us via the contact form if you would like us to look at any other GitHub ethical hacking tools.