CrackMapExec(CME) is a post exploitation tool that can be used for tasks like cracking administrative rights and mapping active directory networks. Active directory is a windows OS utility that provides services like protocols to access other directories in the network, security services through SSL and Kerberos authentication, organizational data storage in a centralized location, and making data available to the network servers with concurrent updates. CME is packed with different sub-modules including Impacket, Powersploit, Invoke-Subfuscation, Invoke-Vnc, Mimikittenz, NetRipper, SessionGopher, RandomPS-Scripts, MimiPenguin, Pywerview, and Pywinrim. These sub-modules work along with the CME protocols, such as http, smb, mssql, and winrm. For example, Impacket and Powersploit work with the network protocols in the post exploitation techniques. Besides post-exploitation, CME has the blue team features as well, such as assessing account privileges, identifying networks misconfigurations, and simulating attacks.
CME Installation
CME is supported by Linux and Mac OSX. In Kali Linux, the tool can be installed using the following commands.
git clone --recursive https://github.com/byt3bl33d3r/CrackMapExec cd CrackMapExec python setup.py install
The –recursive argument in the git command automatically downloads all the sub-modules packages in CME directory. However, if any sub-module gives an error while running the tool, reinstall the sub-module separately to resolve the issue.
It is recommended to use pipenv to avoid any conflicts between the system’s and CME packages. The following commands need to be run to install CrackMapExec using pipenv.
apt-get install -y libssl-dev libffi-dev python-dev build-essential pip install --user pipenv git clone --recursive https://github.com/byt3bl33d3r/CrackMapExec cd CrackMapExec && pipenv install pipenv shell python setup.py install
Running CrackMapExec
Once CrackMapExec is installed, it can be executed using the following command.
cme
To see all the available options, run CME with the help command.
cme --help
CME comes with http, ssh, smb, mssql, and winrm protocols. The options available for each protocol can be viewed using the following help command.
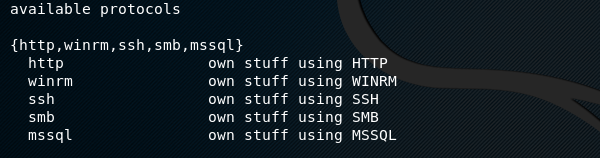
cme <protocol name> --help
To see available set of modules for each protocol, use the –L flag.
cme <protocol name> -L
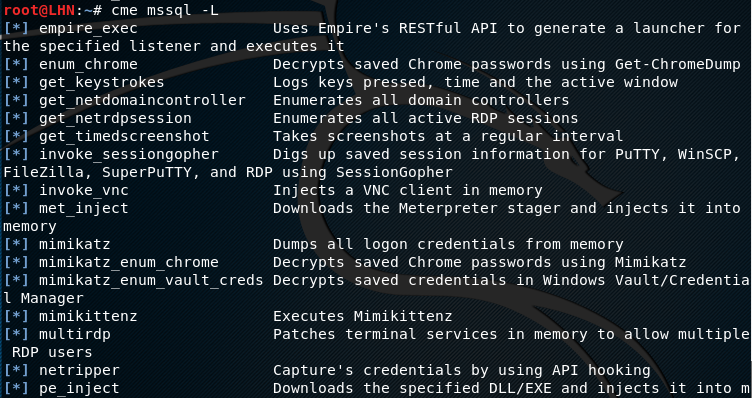
For instance, we can check the available modules for mssql protocol in the following manner.
cme mssql –L
To run the protocol and module together on the target host, use the following command.
cme <protocol name> <target host> -M <module name>
Each module has a set of options that can be explored by using the –options arguments in the following command.
cme <protocol name> <target host> -M <module name> --options
The desired module option can be implemented in the command by using the –o flag in the following manner.
cme <protocol name> <target host> -M <module name> -o <module option>
What Bunny rating does it get?
CME is packed with a number of modules and protocols to map an entire network and gain useful information like admin rights of network machines, usernames, and passwords in the systems’ memory. One of the best features of the tool is maintaining the log file in a database that can be accessed later if required, as a result we will be awarding this tool a rating of 4.5 out of 5 bunnies.




![]()
Want to learn more about ethical hacking?
Do you know of another GitHub related hacking tool?
Get in touch with us via the contact form if you would like us to look at any other GitHub ethical hacking tools.