PrivilegeEsc-Linux is a simple script which checks the security on a Linux machine. It can run many different options, such as for checking the OS version, the environment , the apps and services, the upload options and more. Mainly focus is to enumerate everything it can in a Linux Machine and with this information you can then escalate to root.
Installing PrivilegeEsc-Linux
The repository contains just the script, so clone it and you are good to go.
git clone https://github.com/J4c3kRz3znik/PrivilegeEsc-Linux.git
Running PrivilegeEsc-Linux
Type the commands below to run the script.
cd PrivilegeEsc-Linux/ chmod +x Priv_enum.sh ./Priv_enum.sh
Remember that this script should be used after you have exploited a Linux Machine. So assume that we have already access to a machine and we have uploaded this script into it. To find a writable directory to upload this script, simply type the command below to your victim’s machine.
find / -writable -type d 2>/dev/null
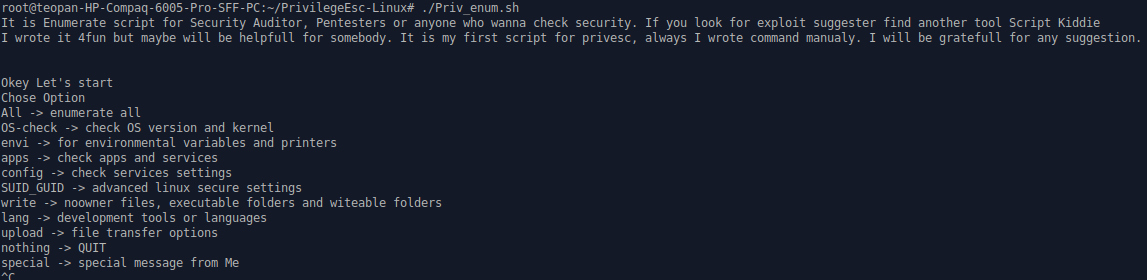
The interface is simple and contains all the options you can run. Just type ‘All‘ to enumerate everything to your victim’s machine. After the scan is finished it shows a vast amount of information about the target. The first thing to have in mind with this tool is that all it does is enumerate the target, not to suggest exploits. So, use this data wisely, and search more based on the information you got.
What Bunny rating does it get?
PrivilegeEsc-Linux is a great script, it can help you a lot with your Privilege Escalation process. Simple and easy, it shows you a lot of different information you can use. Especially, if you are an OSCP student you will understand that this tool is a must have for your work. I’m giving it 4 out of 5 bunnies.




Want to learn more about ethical hacking?
Do you know of another GitHub related hacking tool?
Get in touch with us via the contact form if you would like us to look at any other GitHub ethical hacking tools.
