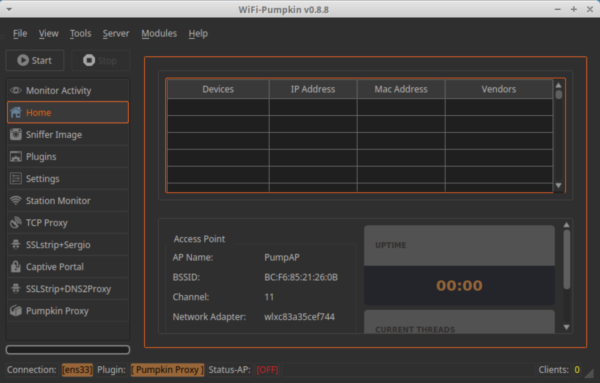
Wifi Pumpkin is a security audit framework used to test the security of wifi against threats like man in the middle attacks. The tool also can create rogue Wi-Fi access points to hack WiFi via deauth attacks on client APs, a probe request and credentials monitor, transparent proxy, Windows update attack, phishing manager, ARP Poisoning, DNS Spoofing, Pumpkin-Proxy, and image capture on the fly.
Wifi Pumpkin Installation
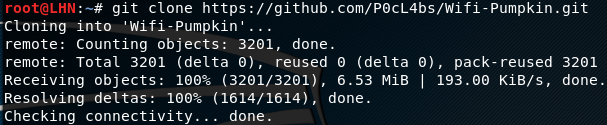
Wifi Pumpkin is supported by Kali Linux, Parrot OS, Pentoo, and Ubunto. Wifi Pumkin can be installed by cloning the framework from github and running the installer as shown in the following commands.
git clone https://github.com/P0cL4bs/WiFi-Pumpkin.git cd WiFi-Pumpkin chmod +x installer.sh sudo ./installer.sh --install
Wifi Pumpkin requires the following software to operate.
- hostapd
- isc-dhcp-server
- php5-cli
- rfkill
- iptables
- Nmcli
Isc-dhcp-server and php5-cli are optional. The dependencies can be installed by running the requirements.txt file as follows.
pip install –r requirements.txt
How Wifi Pumpkin Works
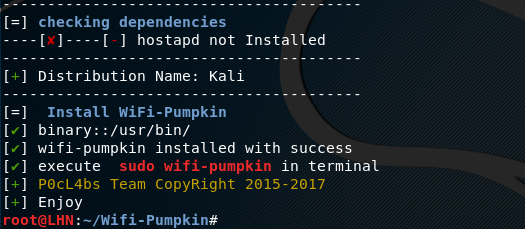
Wifi Pumpkin can be used in many ways. For demonstration purpose, we are going to create a rogue access point where anybody can connect without requiring any credentials. Wifi Pumpkin requires Ethernet and wifi adapter to make wifi access point. Run the following command to check the available wifi interface.
iwconfig
In most of the cases, it is wlan0. The next step is to launch the Wifi Pumpkin. Run the following command to open the Wifi Pumpkin interface.
wifi-pumpkin
If that does not work, run the same command with sudo option i-e
sudo wifi-pumpkin
Once the Wifi Pumpkin interface is opened, go to plugins tab to select the desired plugins for auditing or simulating the wifi attack.
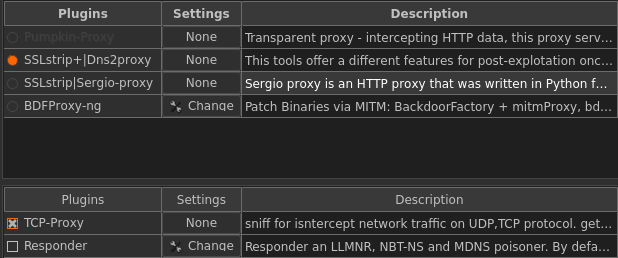
The next step is to configure the access point from the settings tab. The settings tab offers different configurations to adapt, such as Access Point setting (configuring SSID and BSSID, choosing the network adapter), activity monitor setting, and DHCP setting. In the settings tab, there is an option of enabling the wireless security. Keep it unchecked for creating rogue access point without any credentials.
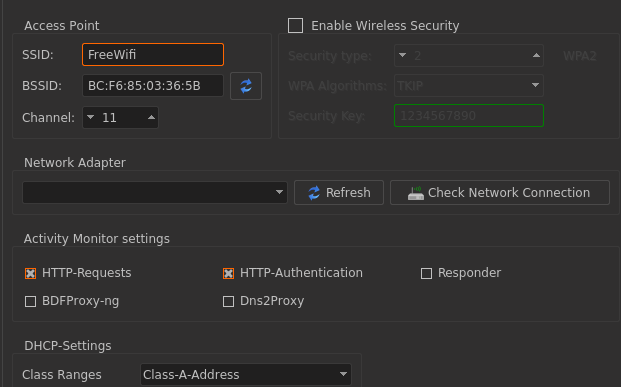
After the settings are complete, hit the start button to allow the access point to broadcast the free wifi in the vicinity. Wifi Pumpkin has an activity monitoring window that captures all the traffic of the users who are connected with the rogue access point.
What Bunny rating does it get?
Wifi Pumpkin is a decent penetration testing framework that can easily simulate wifi attacks for security assessments. The GUI interface makes the framework usage less technical. As a result we will be awarding this tool a rating of 4 out of 5 bunnies.




Want to learn more about ethical hacking?
We have a networking hacking course that is of a similar level to OSCP, get an exclusive discount here
Help support LHN by buying a T-shirt or a mug?
Check out our selection here
Do you know of another GitHub related hacking tool?
Get in touch with us via the contact form if you would like us to look at any other GitHub ethical hacking tools.