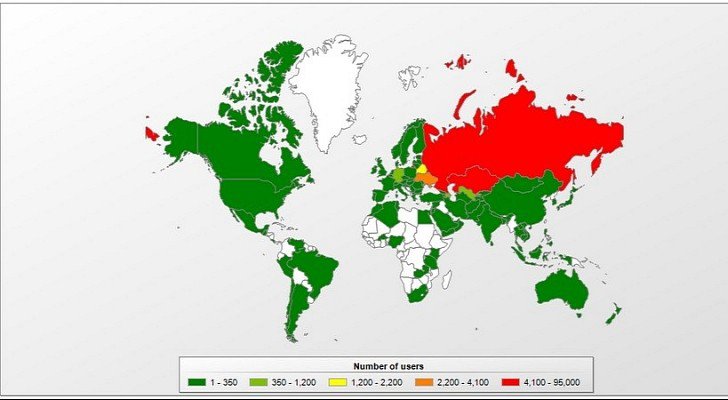
Most of the infections have been spotted in Russia, but researchers have determined that Trojan-SMS.AndroidOS.Stealer.a is capable of targeting users from numerous countries, including Belgium, France, Latvia, Lithuania, Ukraine, Belarus, Germany, Armenia, Azerbaijan, Kyrgyzstan and Kazakhstan.
The Trojan, which cybercriminals distribute by disguising it as legitimate Android apps, contacts its command and control server (C&C) and waits for commands. The C&C can command it to change the server, send SMSs, delete incoming messages, update itself, upload information on the phone and applications, and intercept messages.
What’s interesting about the threat is that its configuration file is distributed along with the malware, instead of being hosted somewhere online. This enables the Trojan to operate even if it can’t find a connection to the Web.
The configuration file can order the malware to open a web page, get geographic coordinates, send SMSs with a certain message to a specified number, install applications, create shortcuts and more
Full description of the commands accepted by Trojan-SMS.AndroidOS.Stealer.a is available on Kaspersky’s Securelist blog.